EBS CSI driver installation
The Amazon Elastic Block Store (Amazon EBS) Container Storage Interface (CSI) driver manages the lifecycle of Amazon EBS volumes as storage for the Kubernetes Volumes that you create. The Amazon EBS CSI driver makes Amazon EBS volumes for these types of Kubernetes volumes: generic ephemeral volumes and persistent volumes.
Pre-requisites
- EKS cluster and access to EKS cluster through
awscli - Export the below variables
export CLUSTER_NAME="" export AWS_REGION="" export AWS_ACCOUNT_ID=$(aws sts get-caller-identity --query "Account" --output text) export OIDC_ENDPOINT=$(aws eks describe-cluster --name ${CLUSTER_NAME} \ --query "cluster.identity.oidc.issuer" --output text)
Creating the IAM role
- Create the following policy document
cat > ebs-assume-role-policy.json <<EOF { "Version": "2012-10-17", "Statement": [ { "Effect": "Allow", "Principal": { "Federated": "arn:aws:iam::${AWS_ACCOUNT_ID}:oidc-provider/${OIDC_ENDPOINT#*//}" }, "Action": "sts:AssumeRoleWithWebIdentity", "Condition": { "StringEquals": { "${OIDC_ENDPOINT#*//}:aud": "sts.amazonaws.com", "${OIDC_ENDPOINT#*//}:sub": "system:serviceaccount:aws-ebs-csi-driver:ebs-csi-controller-sa" } } } ] } EOF - Create the role using the below command
# Create the role aws iam create-role \ --role-name AmazonEKS_EBS_CSI_DriverRole-${CLUSTER_NAME} \ --assume-role-policy-document file://"ebs-assume-role-policy.json" # Attach the policy aws iam attach-role-policy \ --policy-arn arn:aws:iam::aws:policy/service-role/AmazonEBSCSIDriverPolicy \ --role-name AmazonEKS_EBS_CSI_DriverRole-${CLUSTER_NAME}
Installing the AWS EBS CSI driver
-
Head over to the platform and connect the cluster if you haven't connected it to the TrueFoundry's platform.
-
From the left panel go to the Integrations tab and click on Manage Applications from the the three dots in the right bottom corner of the cluster card.
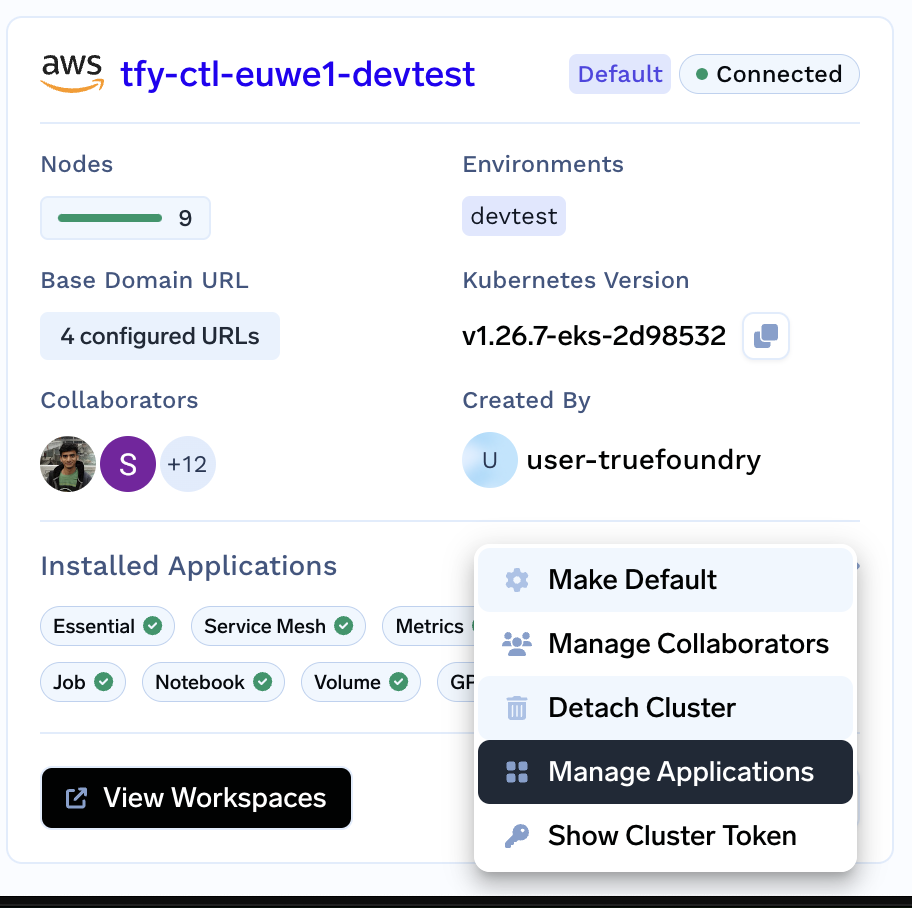
-
Go to the Volumes Section and click on
+InstallagainstAws Ebs Csi Driver

-
Click on
Create Workspaceon the next screen followed byCreateto leave the settings of the workspaceaws-ebs-csi-driveras default. -
In the next screen enter the Role ARN at line 7
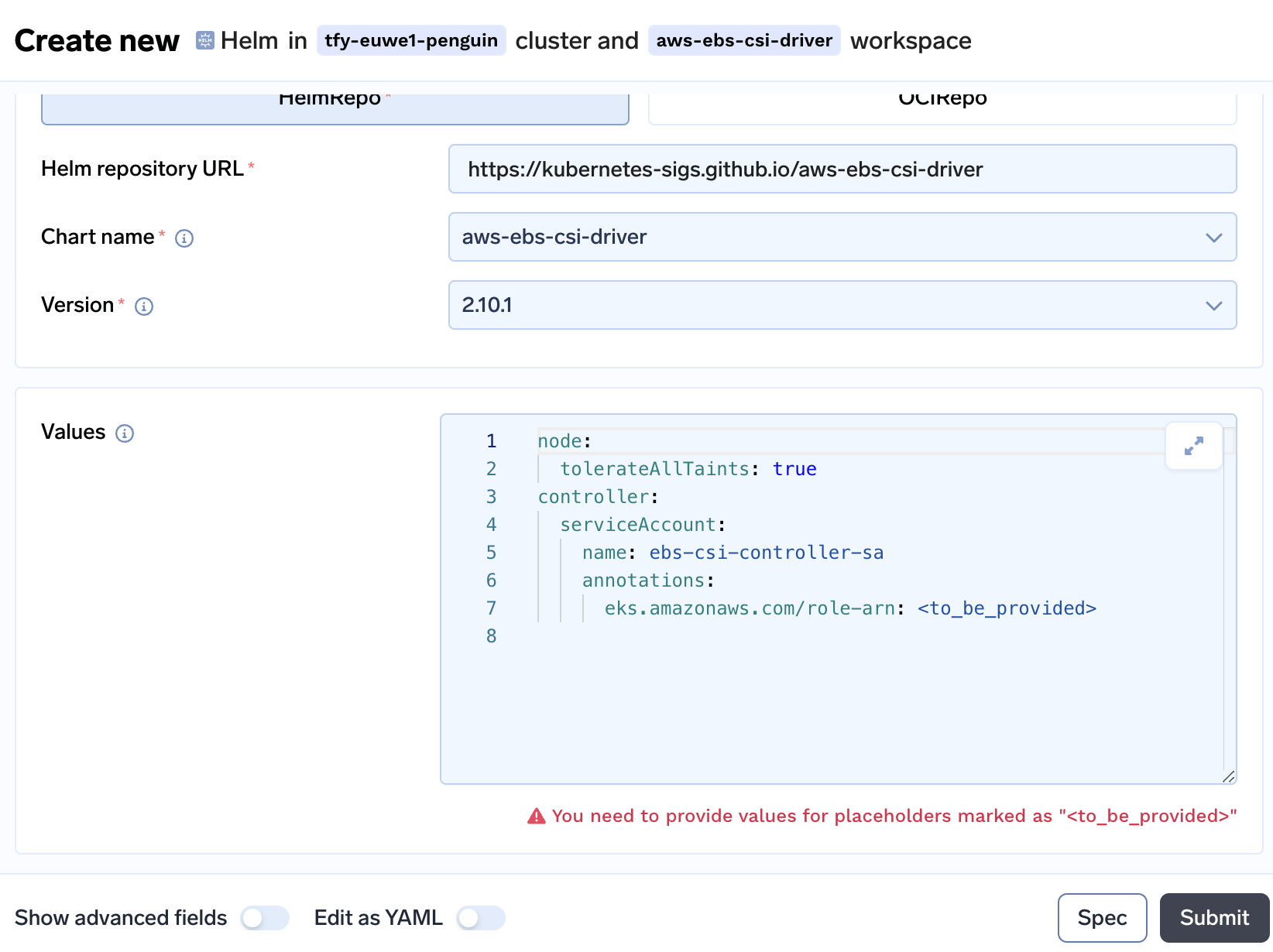
-
Following is an example
node: tolerateAllTaints: true controller: serviceAccount: name: ebs-csi-controller-sa annotations: eks.amazonaws.com/role-arn: arn:aws:iam::XXXXXX:role/AmazonEKS_EBS_CSI_DriverRole-CLUSTER_NAME
Updated 4 months ago