Overview
An air-gapped environment is isolated from internet. This means all the artifacts(helm charts, container images) needed for the platform to work have to be made available locally or in an internal network without access to the internet. We do this by pushing all the images and helm charts to a dedicated OCI compatible container registry which should be accessible from the environment where the cluster is supposed to run. We have provided a list of images and a script to pull and push those images to any other registry. You will also need to provide access to annpm registry with js-yaml package hosted from within the cluster.
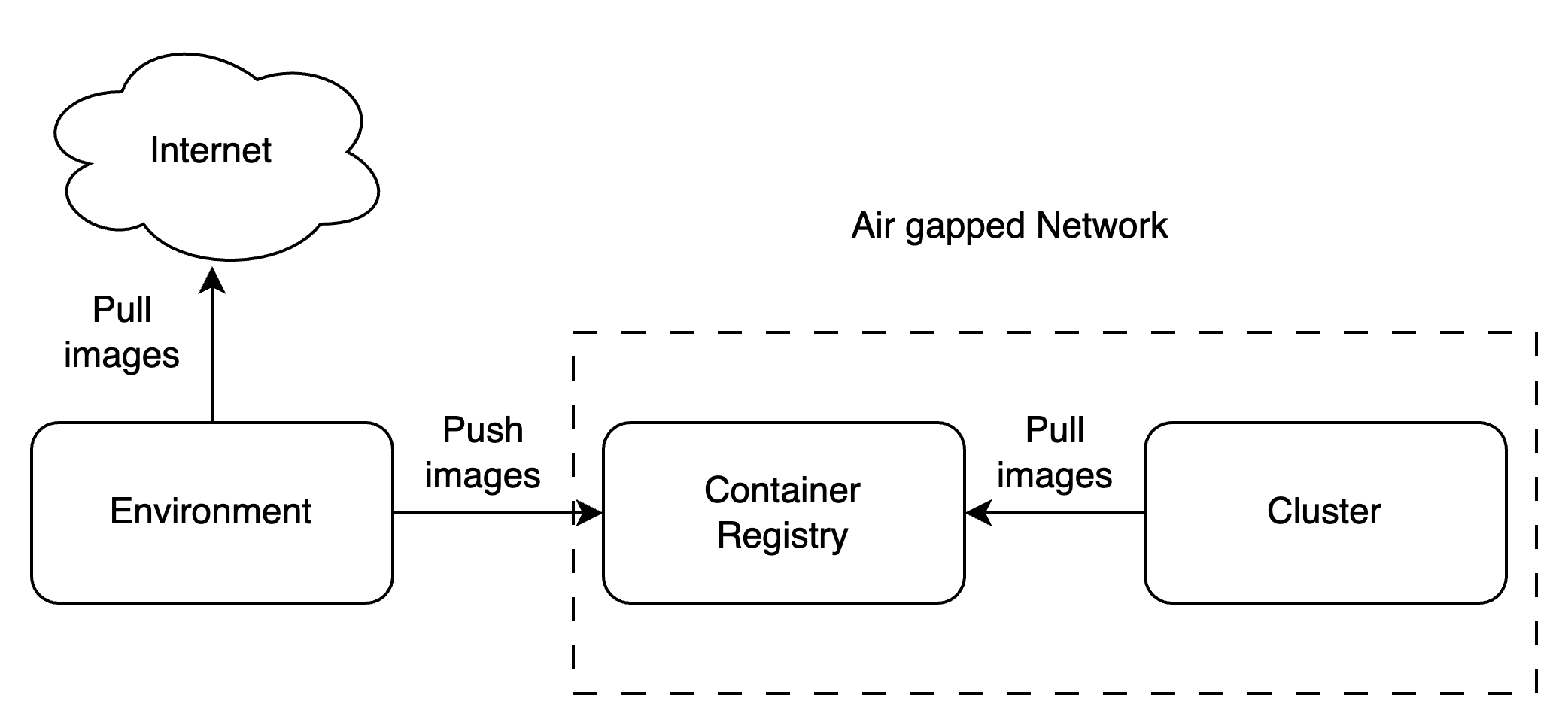
Requirements
In order to setup TrueFoundry in an air-gapped environment, the following are needed-
An OCI compatible registry which should be able to serve the following (you can also reuse the TrueFoundry’s registry at
tfy.jfrog.io/tfy-imagesfor container images andtfy.jfrog.io/tfy-helmfor helm charts instead of replicating the images locally)- OCI compatible images with a username password or any other authentication mechanism that is suitable
- OCI compatible helm charts without authentication
- A secure environment that has access to the internet and image push access to the target registry. This is to push the images to the registry and will be required for initial setup and all upgrades
-
The following should be installed in the environment to run the script
- Python
- Docker
- Helm
- Kubectl
- If running on AWS, karpenter needs access to certain APIs which have to be enabled on private VPC endpoints. Detailed instructions are available here
Uploading artifacts to a private registry
A list of images and helm charts needed by a TrueFoundry installation is maintained in infra-chart repo. Here is a list of TrueFoundry Helm Charts that can be deployed depending on the environment you wish to deploy TrueFoundry into- AWS EKS (tfy-k8s-aws-eks-inframold)
- Azure AKS (tfy-k8s-azure-aks-inframold)
- Civo Talos (tfy-k8s-civo-talos-inframold)
- GCP GKE Standard (tfy-k8s-gcp-gke-standard-inframold)
- Generic Kubernetes Cluster (tfy-k8s-generic-inframold)
Push images and helm charts to the Registry
-
To start download the artifacts manifest file of the helm chart from the list above and save in a local file. This file contains all the container images and helm charts needed for a TrueFoundry installation
-
You must login to the target registry using the
dockerCLI -
To pull and push these images to your own registry, we have provided a sample python script here. Steps to prepare the environment -
-
Clone the
truefoundry/infra-chartsrepo -
Create a virtual env to run the python script in
-
Install the
requirements.txt
-
Clone the
-
The
upload_artifact.pyscript takes in the following argumentsartifact_type- this takes in the artifact type which can be eitherimageorhelmfile_path- this is the location of theartifacts-manifest.jsonfile that contains the details for all the container images and helm charts that are needed for the installationdestination_registry- this is the registry you plan to use in your air-gapped environment
-
Run script with the target container registry details
Deploying Inframold Charts
- Create a namespace for jspolicy
-
If your registry needs to be authenticated before you can pull images, then you have to authenticate the pods to pull the images. Create a secret with the registry auth information
-
Create a file called
jspolicy-values.yamlwith the following content - Install jspolicy helm chart
- Install the
ArgoCDCRDs. These need to be installed first because theJSPolicyresources reference theArgoCDCRD
-
Install
tfy-jspolicy-configChart to patch your images-
Create a file called
jspolicy-config-values.yamlwith the following content. Make sure to add the registry url with proper protocol forreplaceArgoHelmRepo.registryReplacementMap -
Install the tfy-jspolicy-config chart
-
Create a file called
- Now the cluster is ready and you can continue with the appropriate installation steps from here