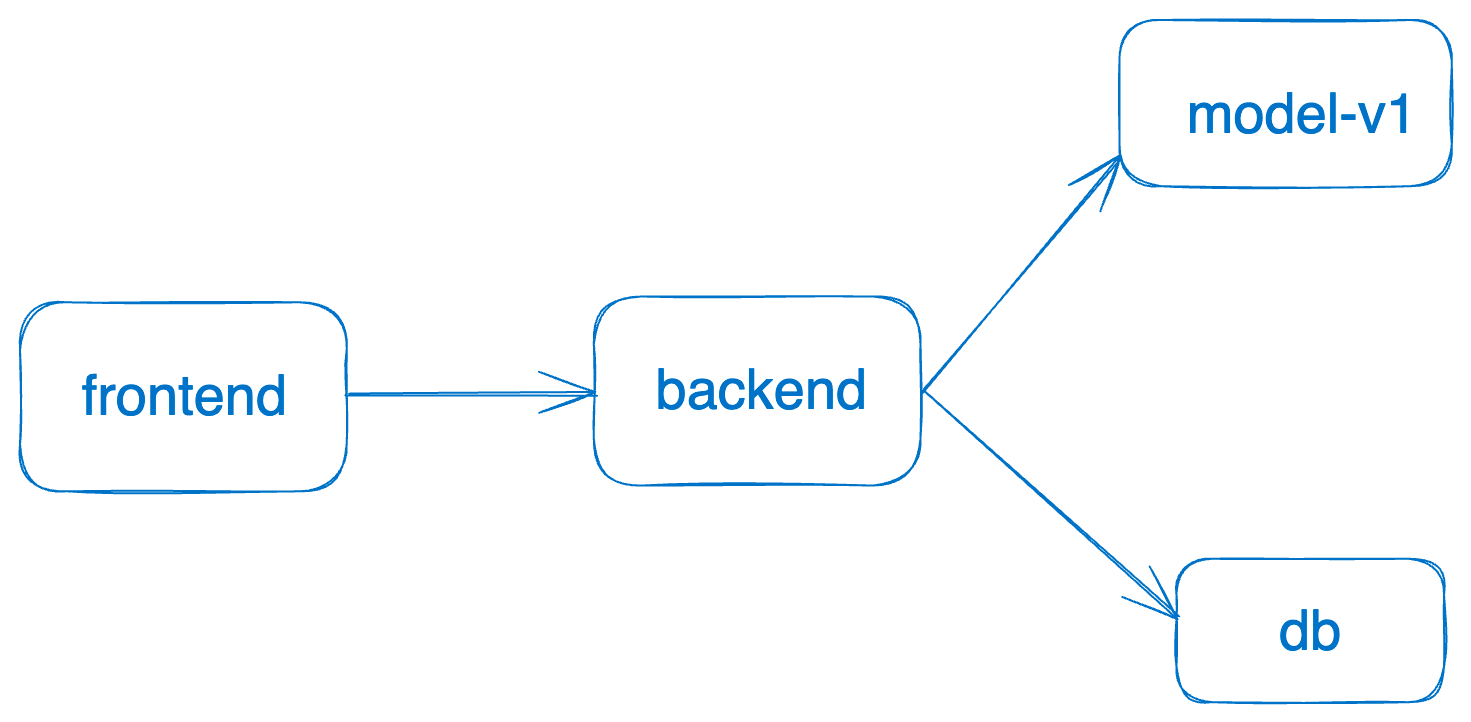
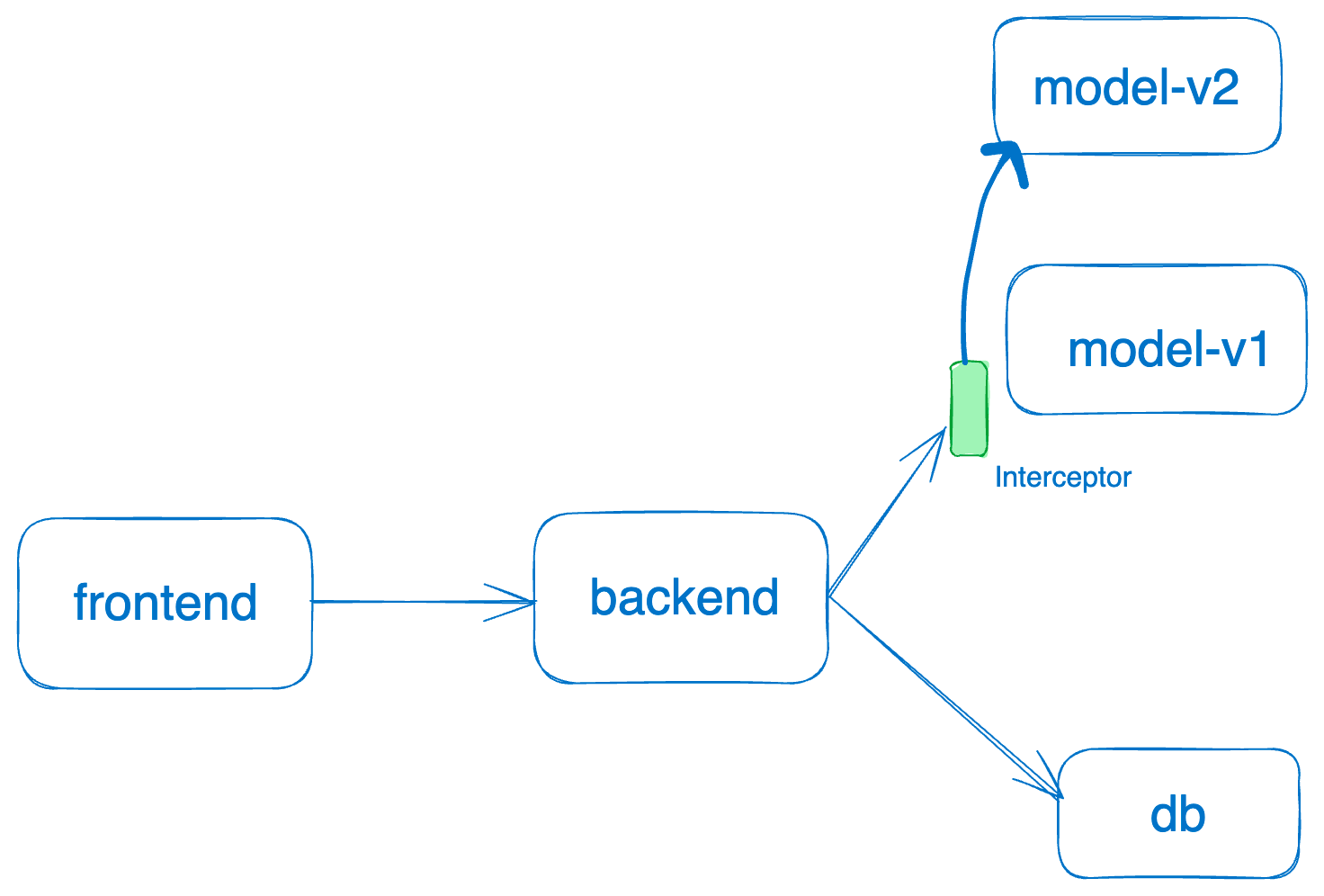
Using UI
- Before intercepts can be enabled for a service, we need to allow intercepts for that service.
- We now can start adding intercept rules
- To test the intercept you can send a request to the service with the header set to the value in intercept rule and verify that the request indeed lands on the service set as destination. Eg -
curl -H "<header name>: <header value>" https://<service endpoint>. If the intercept rules don’t match, the request will continue to go to the original service.