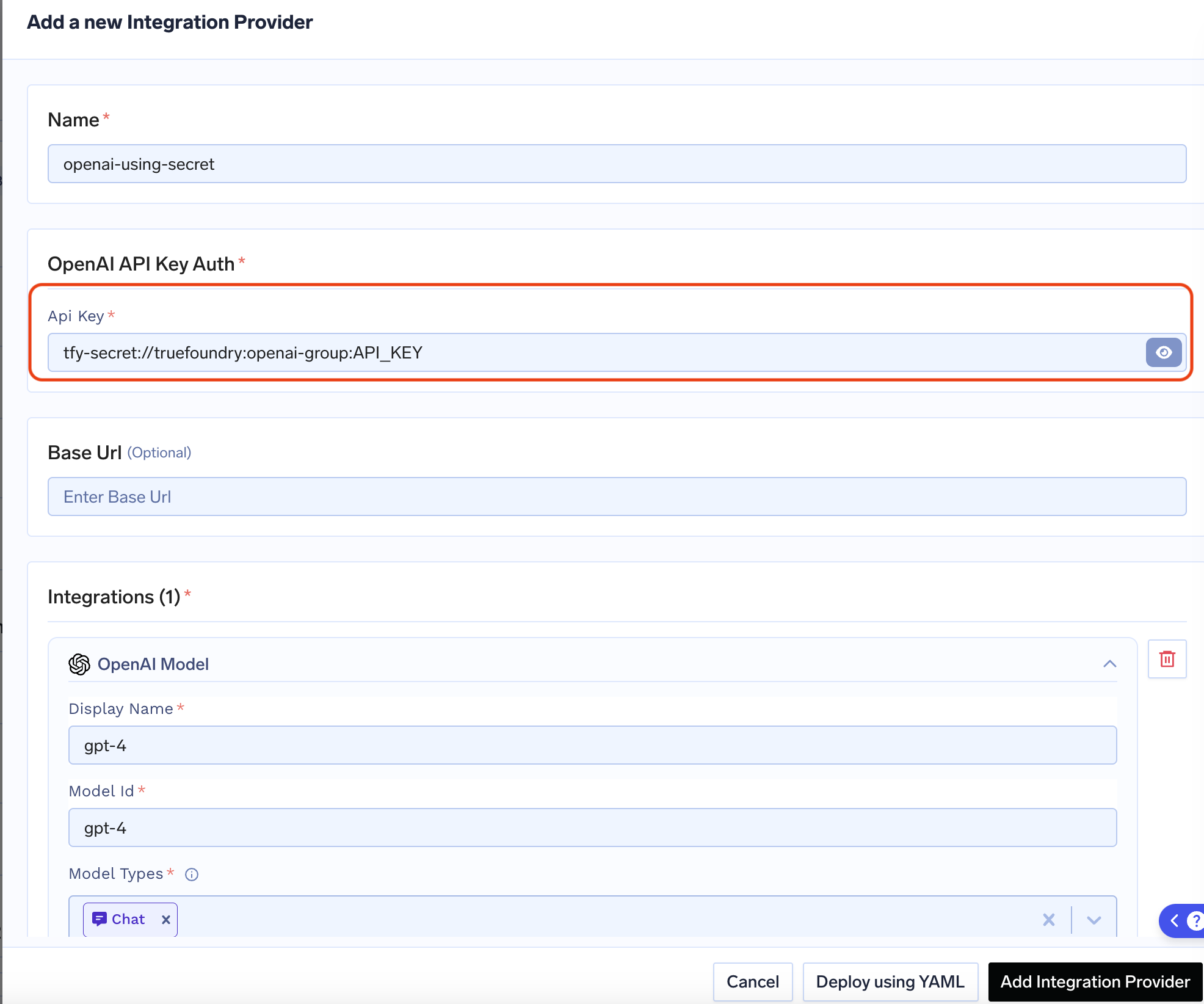
When you save a secret using Truefoundry’s UI, the actual secrets are stored in your SecretManager and Truefoundry never stores the secret with itself. You will then get a fqn (fully-qualified-name) for your secret which you can then use in your deployments.
Creating and Managing Secrets
In a project, you likely have a set of secrets associated with it. Managing access to each individual secret can become cumbersome. Hence, we have the concept of secret groups which lets you organize and manage related secrets for a specific project. Within a Secret Group, you can easily add, remove, and update secrets. You can configure access control on each secret group and grant users/teams read, write or admin access. You can check the demo below on how to add a secret group and some secrets in the group.
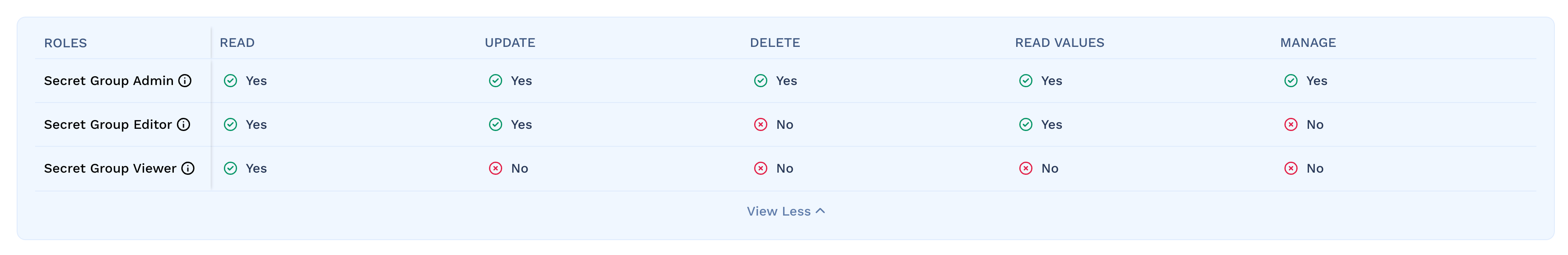
There are 3 roles in Secret groups:
- Secret Group Admin: Can create, edit and delete secrets in the group.
- Secret Group Editor: Can edit and delete secrets in the group and also see the secret values.
- Secret Group Viewer: Can only see the secret keys, but not the values.
By default, a tenant admin has access to all secret groups. For tenant members and teams you need to assign roles for each secret group.
Using the Secrets
Each secret will have a fully-qualified-name (FQN) next to the secret using which you can refer to and use the secret in the places mentioned below.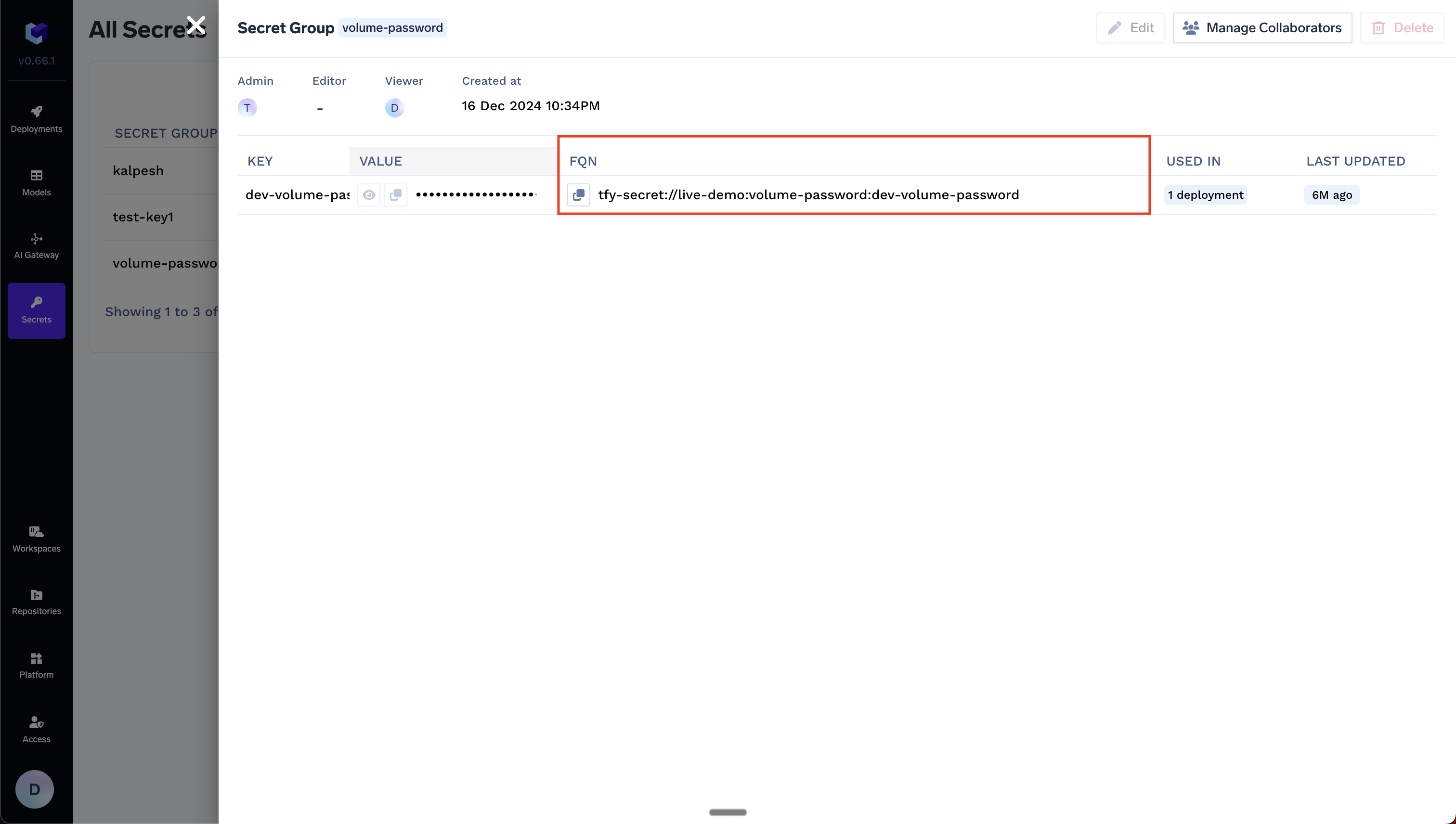
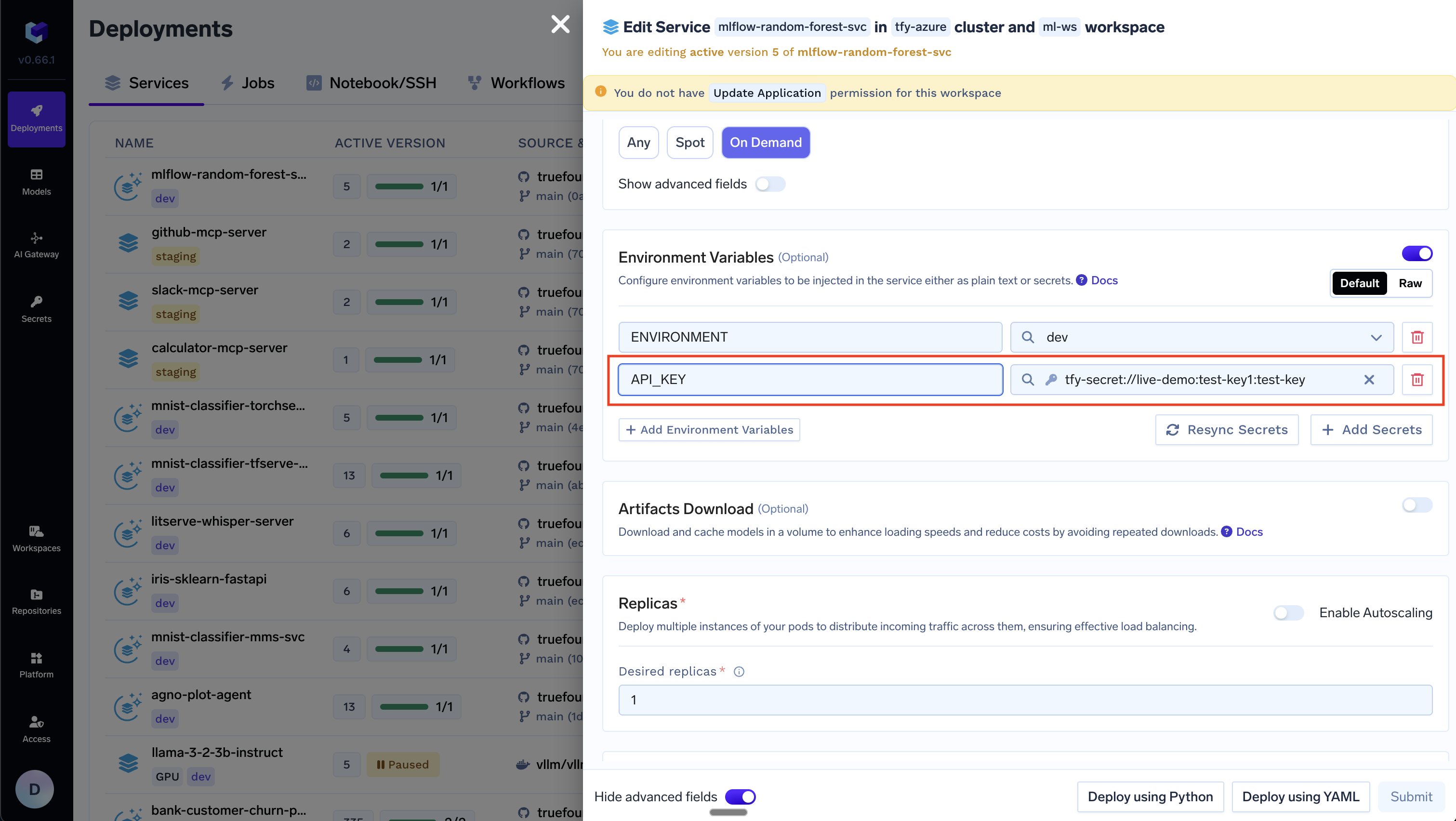
Environment variables in deployments
Environment variables in deployments
Volume Mounts in deployments
Volume Mounts in deployments
You can mount secrets as a volume in your deployments.
API keys / sensitive values in Integrations
API keys / sensitive values in Integrations
API keys for Models in AI Gateway
API keys for Models in AI Gateway