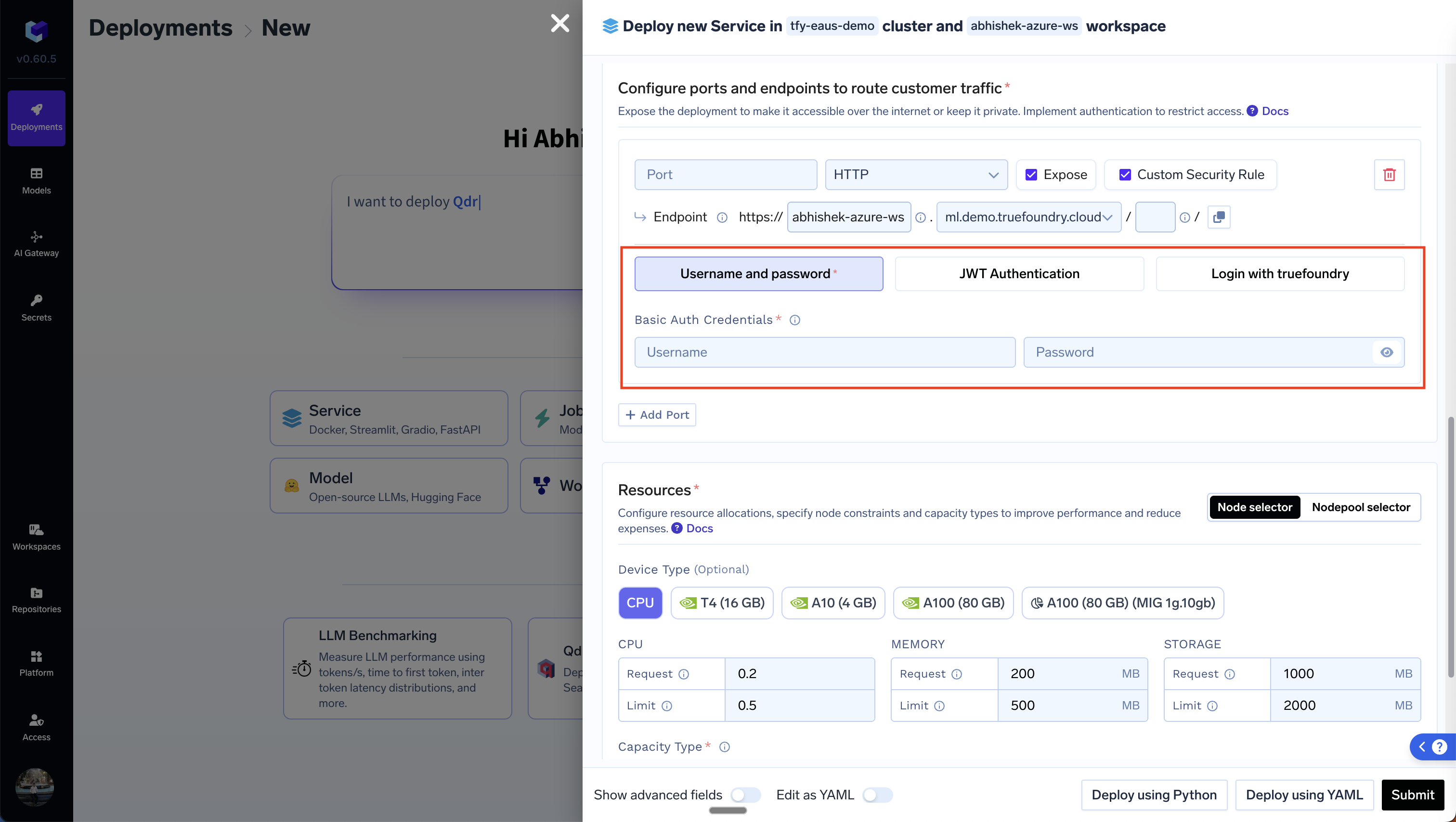
- Username and Password Authentication: In this case, you can provide a username:password combination as a security measure to guard the point. This is very easy to configure but requires passing the credentials around.
- JWT Authentication: In this case, you can provide a JWT token as a security measure to guard the point. In this case, the request to the endpoint will need to have a valid JWT token issued by your identity providers (IDP) like Amazon Cognito, Google, Okta, or Microsoft Entra ID. The gateway will validate the JWT using the public key from the IDP’s JWKS endpoint.
- Login With Truefoundry: In this case, you can provide a Truefoundry login to guard the point. This is very easy to configure by just clicking on the checkbox to enable. In this case, the user will need to be logged in to Truefoundry to be able to access the endpoint.
Username and Password Authentication
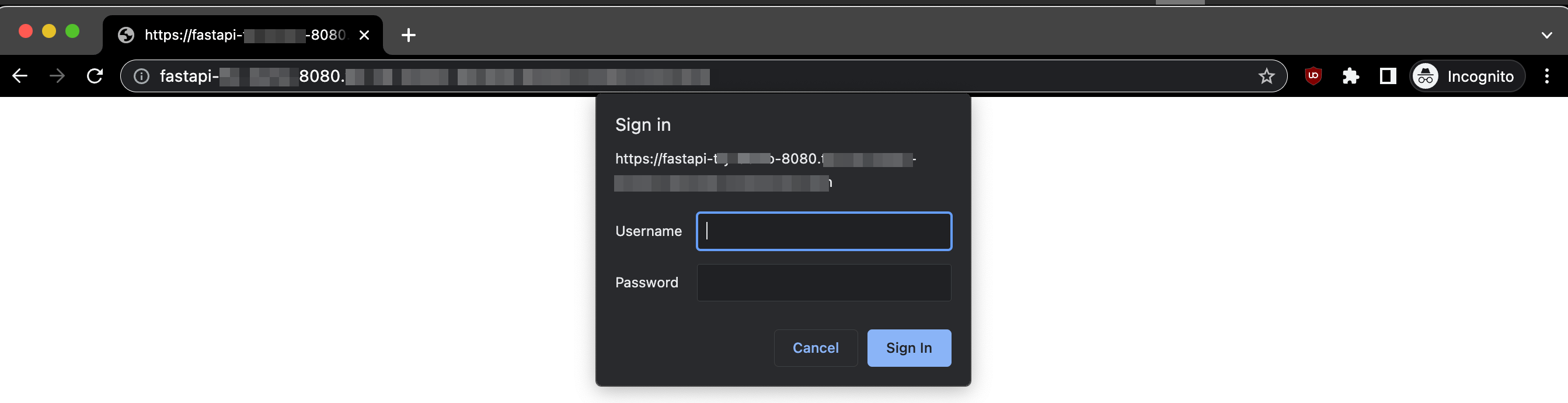
To configure this, please choose theUsername and Password option after clicking on Enable Authentication and provide a value for username and password (Let’s say you set the username to hello and the password to pass). Once you update the deployment, you can access the endpoint with the credentials in the following ways:
- Access via Browser
- Access via Python code
- Access via cURL
JWT Authentication
To setup JWT authentication, we first need to setup a Custom JWT Auth integration that tells Truefoundry how to validate the JWT token and also do login via Oauth in case you want Oauth2 based login for your service.Create a Custom JWT Auth Integration
- Go to the Platform page in the left sidebar and click on Integration Providers. Click on Add Integration Provider button and choose the Custom option.
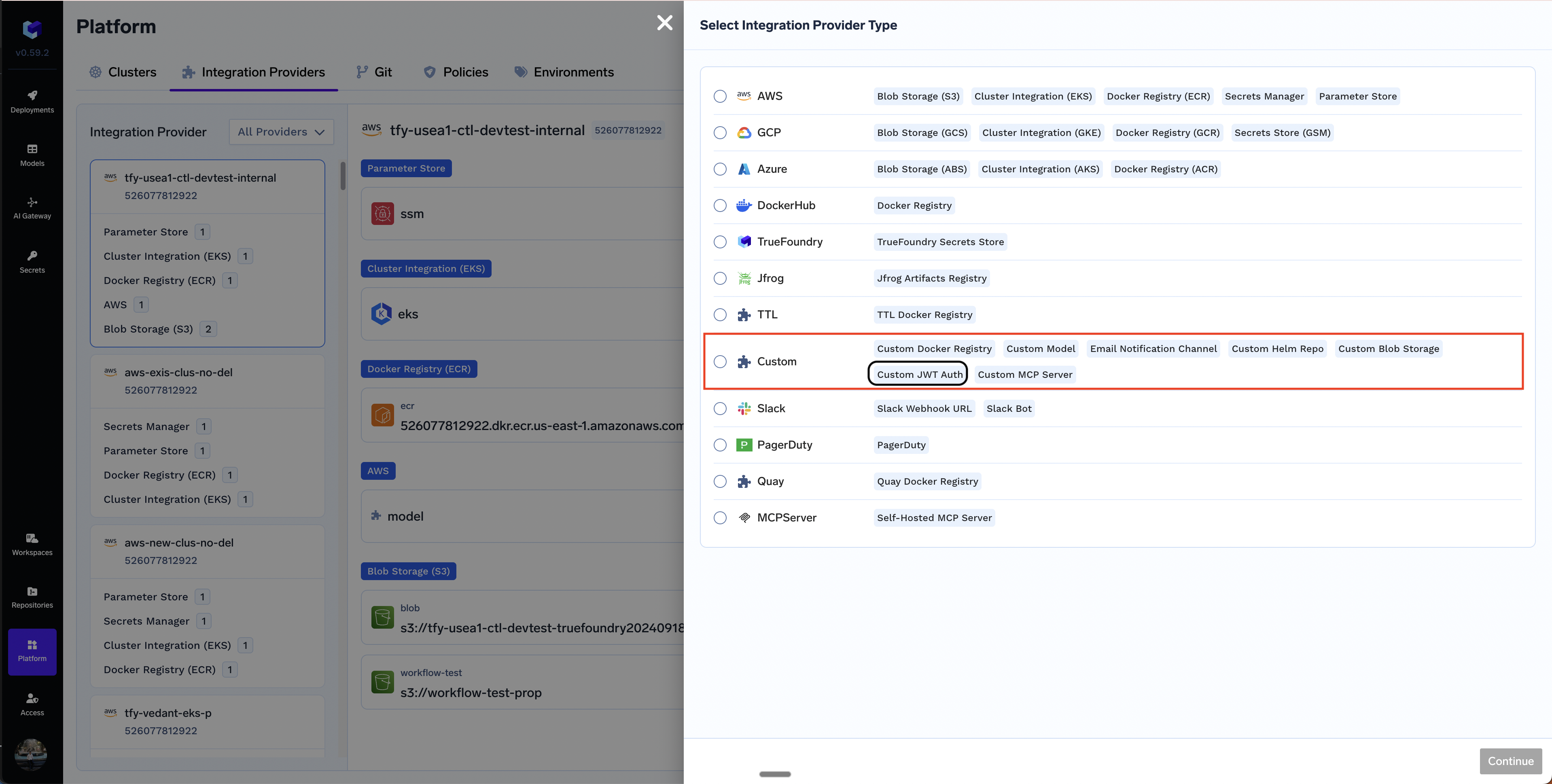
- Provide the following details about the JWT Integration:
- Name: A name to refer to this integration later.
- Issuer: The base URL of the authentication provider
- JWKS URL: The JSON Web Key Set URI for JWT verification.
- Oauth2 Client Configuration (Optional): Enable Login Provider and provide the values for
Client ID,Client Secret,Authorization URL,Token URL, and anyScopes(e.g.openid,profile,email, etc.)
Amazon Cognito
Amazon Cognito
Create a Cognito User Pool
Create an Application
- Choose Traditional Web Application as the Application Type.
- Skip adding the return URL for now - it can be added later after deploying the TrueFoundry service.
- Save ClientID and ClientSecret
Copy Details from OpenID Configuration URL
issuer, jwks_uri, authorization_endpoint, token_endpoint, scopes_supportedIntegrate with TrueFoundry
- Use the values from the previous step in the integration
- For Client Secret, you can either directly add the value in the form or first create a Truefoundry Secret and then use the FQN of the secret.
- Include appropriate scopes as required for your integration (e.g.,
openid,email, etc.). - Retain JWT Source as Access Token (no changes needed).
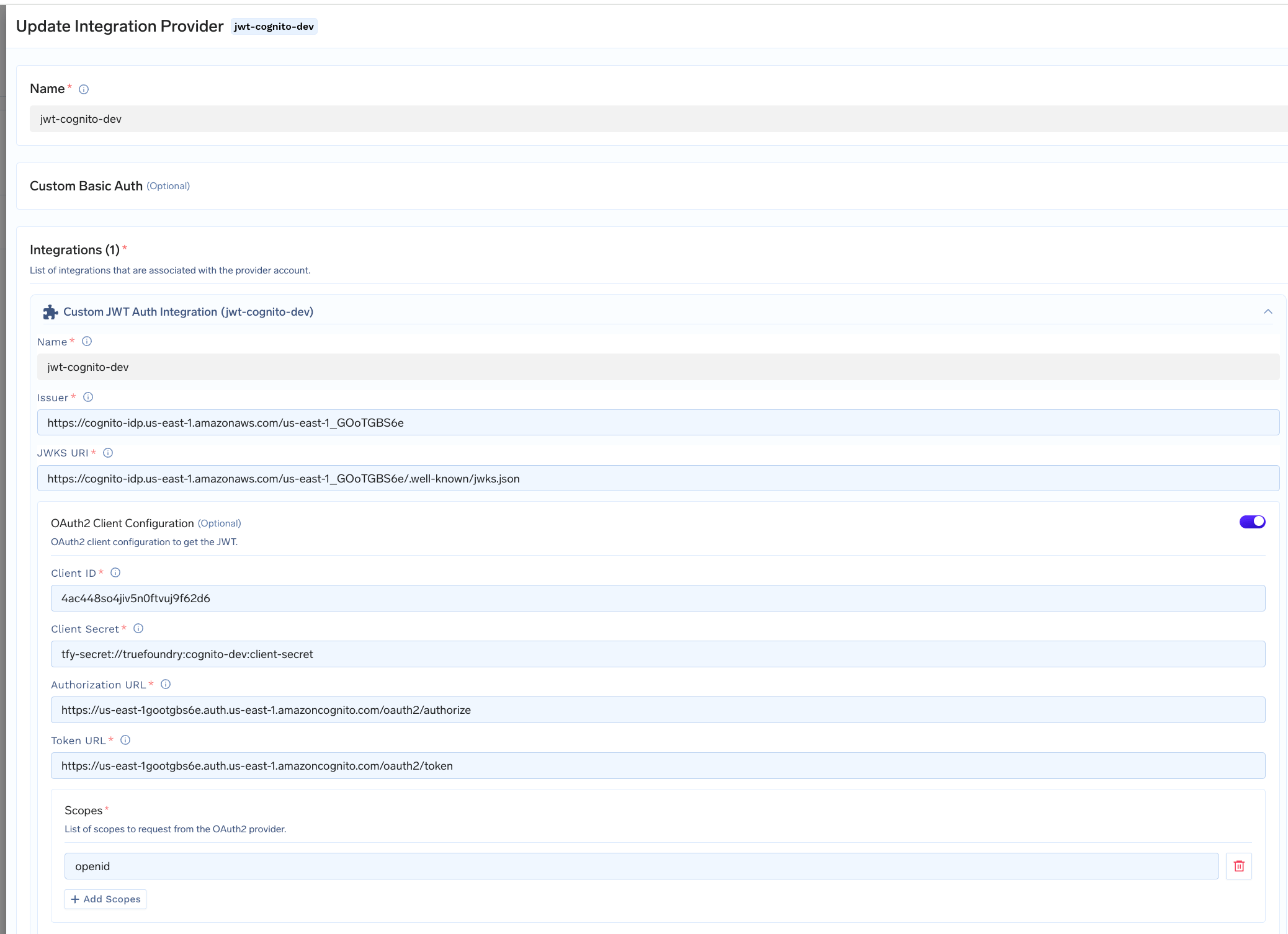
Sample Custom JWT Auth integration for Amazon Cognito
Google OAuth2
Google OAuth2
Create a Google Cloud Project
Enable the OAuth 2.0 API
- Go to APIs & Services > Credentials.
- Click Create Credentials and select OAuth Client ID.
Create an OAuth 2.0 Application
- Choose “Web Application” as the Application Type.
- Skip adding the Authorized Redirect URI for now - it can be added later after deploying the TrueFoundry service.
- Save the Client ID and Client Secret
Copy Details from OpenID Configuration URL
- Open the URL https://accounts.google.com/.well-known/openid-configuration
- Copy the values for
issuer,jwks_uri,authorization_endpoint,token_endpoint,scopes_supported
Integrate with TrueFoundry
- Use the values from the previous step in the integration
- For Client Secret, you can either directly add the value in the form or first create a Truefoundry Secret and then use the FQN of the secret.
- Include the mandatory
openidscope, along with other required scopes (e.g.,emailetc.). - Set JWT Source to
ID Tokeninstead of Access Token.
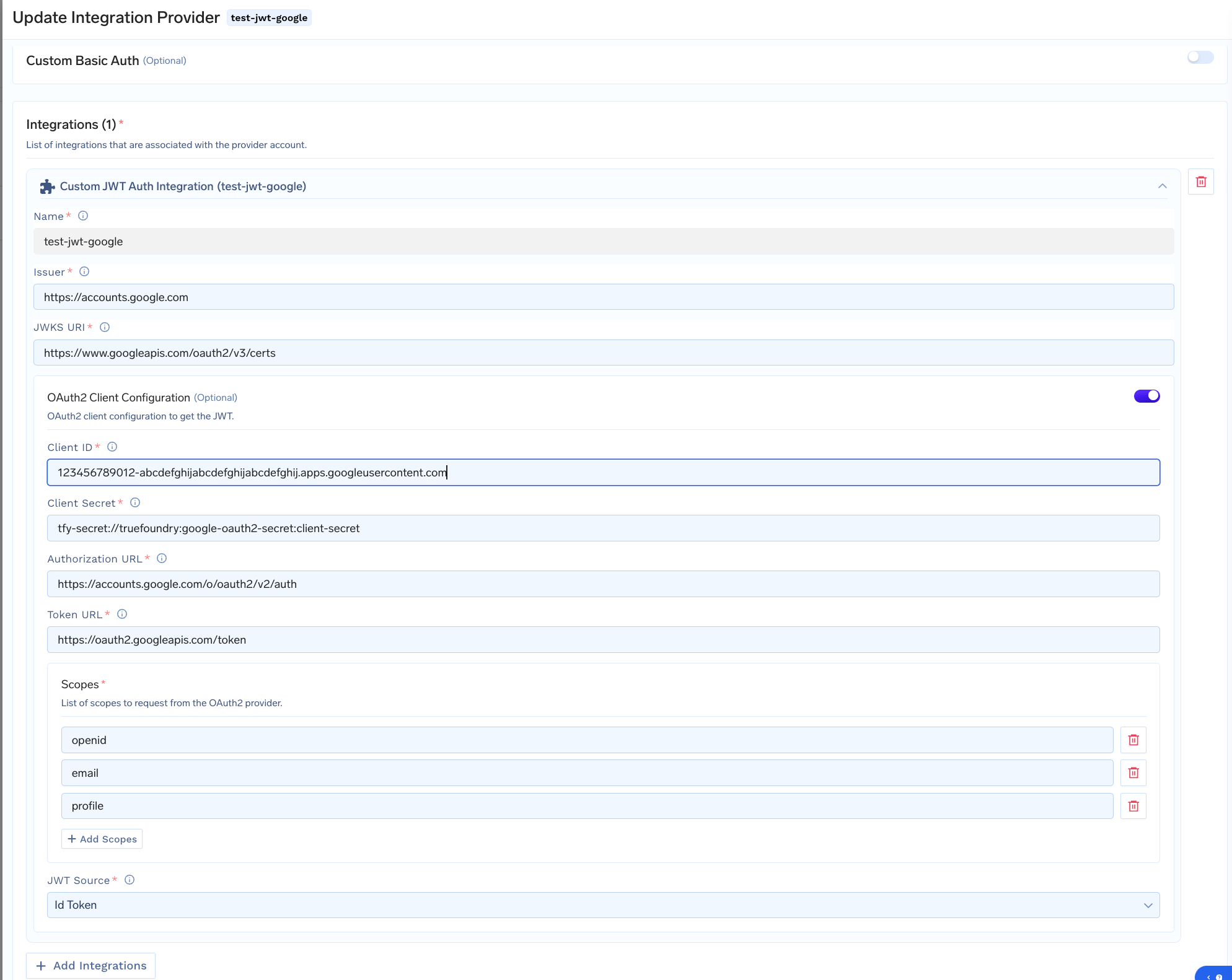
Custom JWT Auth integration for Google OAuth2
Steps
- Create a Google Cloud Project (if not already available) at Google Cloud Console.
-
Enable the OAuth 2.0 API:
- Go to APIs & Services > Credentials.
- Click “Create Credentials” and select OAuth Client ID.
-
Create an OAuth 2.0 Application:
- Choose “Web Application” as the Application Type.
- Skip adding the Authorized Redirect URI for now; it can be added later after deploying the TrueFoundry service.
-
Save the following details:
- Client ID
- Client Secret
-
Open the OpenID Configuration:
-
Example:
-
This contains required fields like:
- Issuer
- JWKS URI
- Authorization URL
- Token URL
- Supported Scopes
-
Example:
Integration with TrueFoundry
- Use the values from the OpenID configuration in the integration.
-
For Client Secret, you can:
- Create a TrueFoundry Secret, or
- Directly add the value.
-
Include the mandatory
openidscope, along with other required scopes (e.g.,emailetc.). -
Set JWT Source to
ID Tokeninstead of Access Token.

Custom JWT Auth integration for Google OAuth2
Okta
Okta
Create an Okta Developer Account
Create an Application
- Choose Web Application as the Application Type.
- Skip adding the Sign-in redirect URI for now - it can be added later after deploying the TrueFoundry service.
- Save ClientID, Client Secret and Okta Domain (e.g.,
https://dev-123456.okta.com)
Copy Details from OpenID Configuration URL
- Open the URL https://dev-123456.okta.com/.well-known/openid-configuration
- Copy the values for
issuer,jwks_uri,authorization_endpoint,token_endpoint,scopes_supported
Integrate with TrueFoundry
- Use the values from the previous step in the integration
- For Client Secret, you can either directly add the value in the form or first create a Truefoundry Secret and then use the FQN of the secret.
- Include appropriate scopes as required for your integration (e.g.,
offline_access,openid,email, etc.). - Retain JWT Source as Access Token (no changes needed).
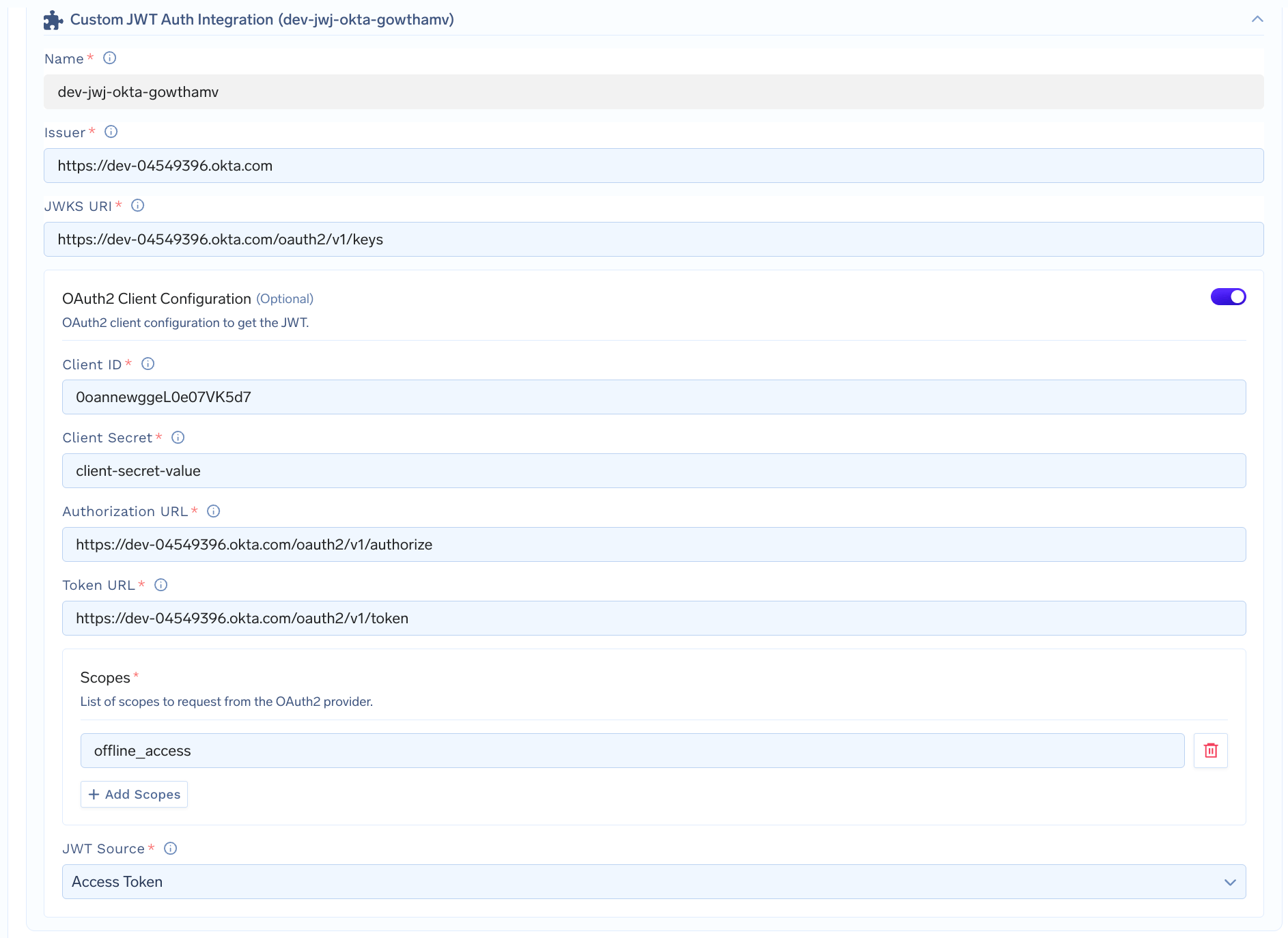
Custom JWT Auth integration for Okta
Microsoft Entra ID (Azure AD)
Microsoft Entra ID (Azure AD)
Create an Azure AD Application
- Follow the Microsoft Entra ID guide to create an application or use an existing one.
- Save the Client ID, Client Secret and Tenant ID.
- Skip adding the redirect URI initially. This can be added later once the TrueFoundry service deployment is created.
Copy Details from OpenID Configuration URL
- Open the URL https://login.microsoftonline.com//.well-known/openid-configuration
- Copy the values for
issuer,jwks_uri,authorization_endpoint,token_endpoint,scopes_supported
Integrate with TrueFoundry
- Use the values from the previous step in the integration
- For Client Secret, you can either directly add the value in the form or first create a Truefoundry Secret and then use the FQN of the secret.
- Include the mandatory
openidscope, along with other required scopes (e.g.,email,profile, etc.). - Set JWT Source to
ID Token
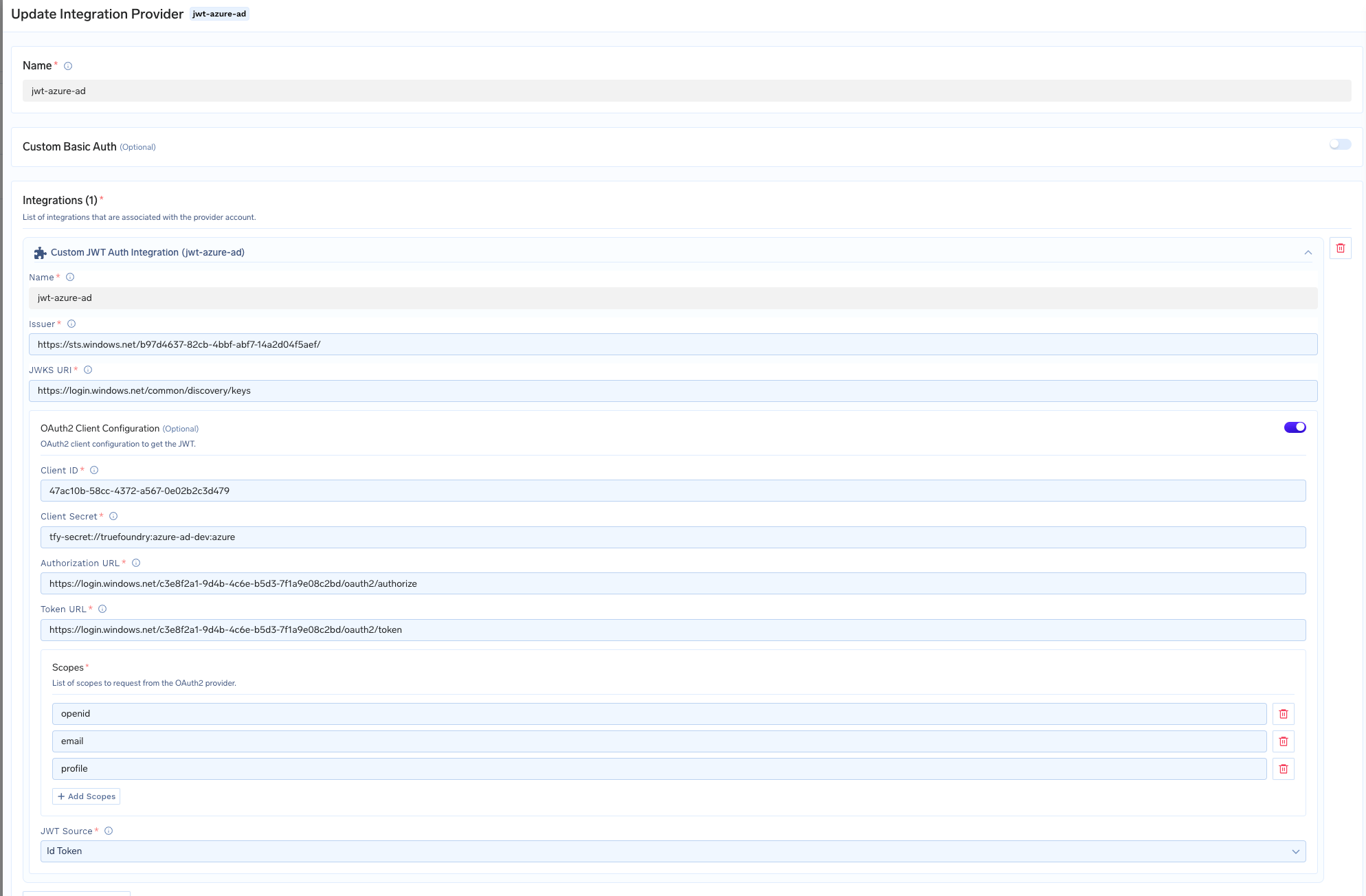
Custom JWT Auth integration for Azure AD/Microsoft Entra ID
Enabling JWT Authentication in Your Service
Once you have set up the Custom JWT Auth integration, you can selectEnable Authentication in the Ports section and choose JWT Integration from the options below.
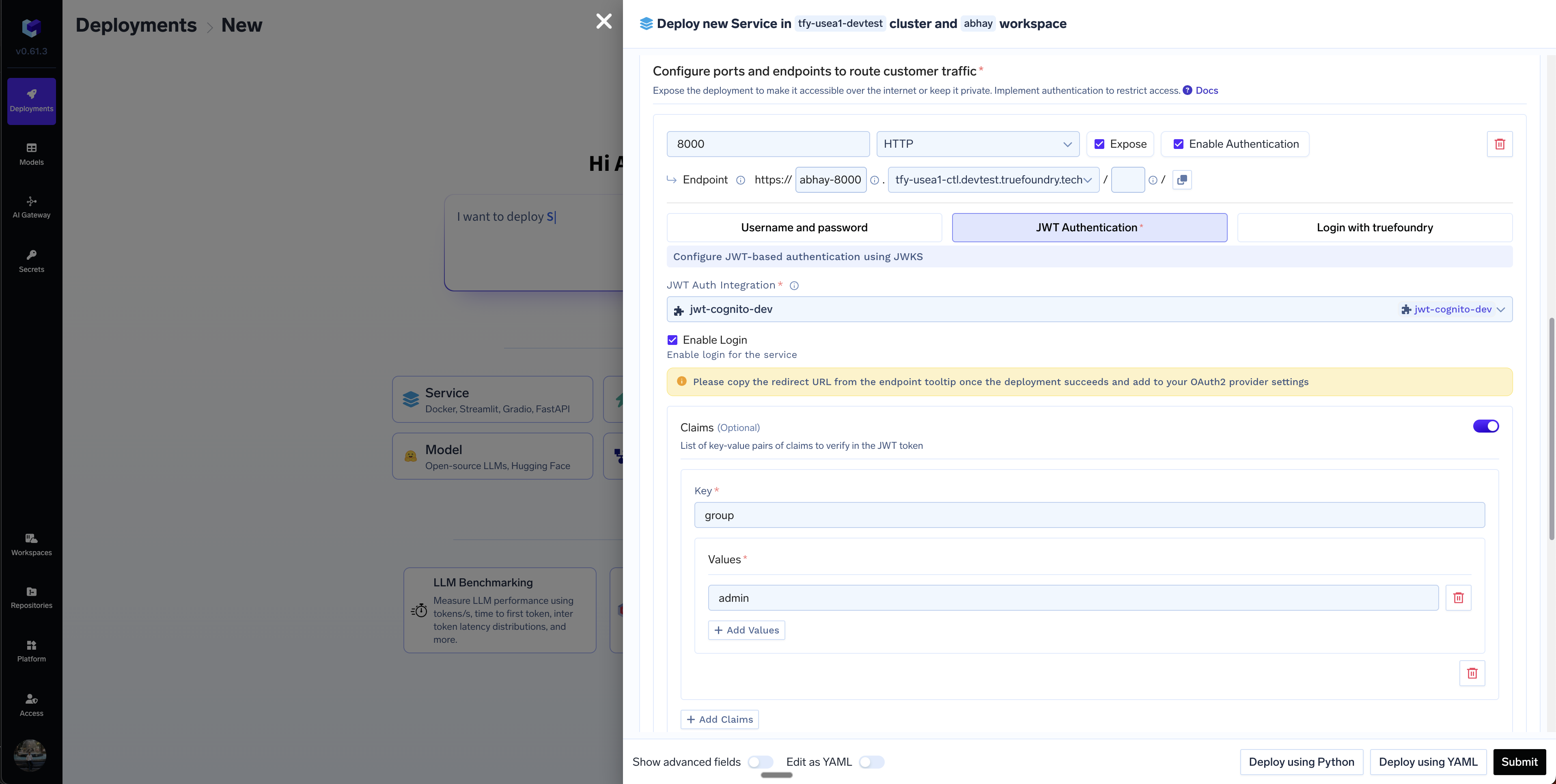
Sample JWT Auth Config while deploying a service
-
You can enforce additional security by verifying claims in the token by providing the key and the accepted values for that key. For e.g. if we want to restrict access to users with emails from
truefoundry.com, we can provide key asemailand accepted values as*@truefoundry.comin the Claims section. -
If OAuth2-based login is enabled, you must configure the Redirect URL in your OAuth2 provider settings.
- After deploying the service, the Redirect URL will be displayed on the deployment page.
- Copy this URL and add it to your OAuth2 provider’s redirect URIs section.
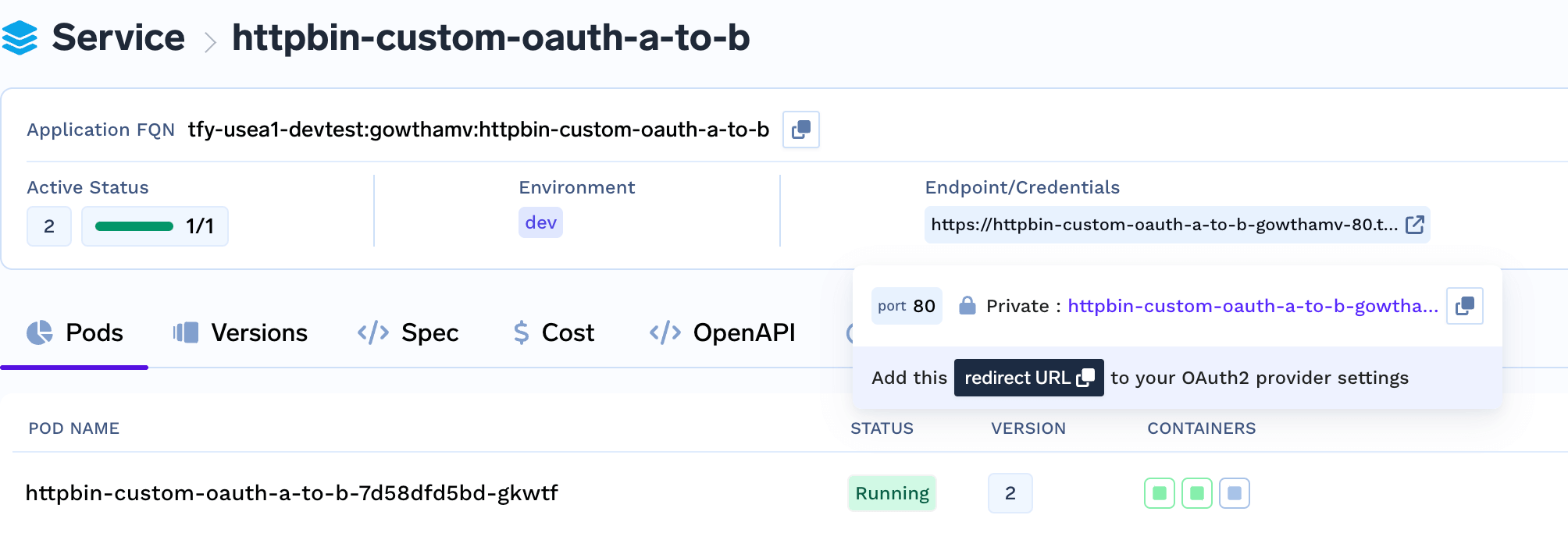
Redirect URL for OAuth2 Login
Sending request to your Authenticated Endpoint
While sending request to an endpoint with JWT authentication enabled, you need to provide the token in theAuthorizationheader. This header carries the token, allowing your service to verify and authenticate the request based on the credentials and claims present in the JWT.
Here is an example of how to send a request using curl:
403. Login with Truefoundry
If you want a quick solution to enable authentication for your service - and the users are all Truefoundry users - you can enable login with Truefoundry. In this case, the users will be prompted with a Login to Truefoundry screen and after authentication, they will be redirected to your application. To enable this, you need to tickEnable Authentication and select Login with Truefoundry option.
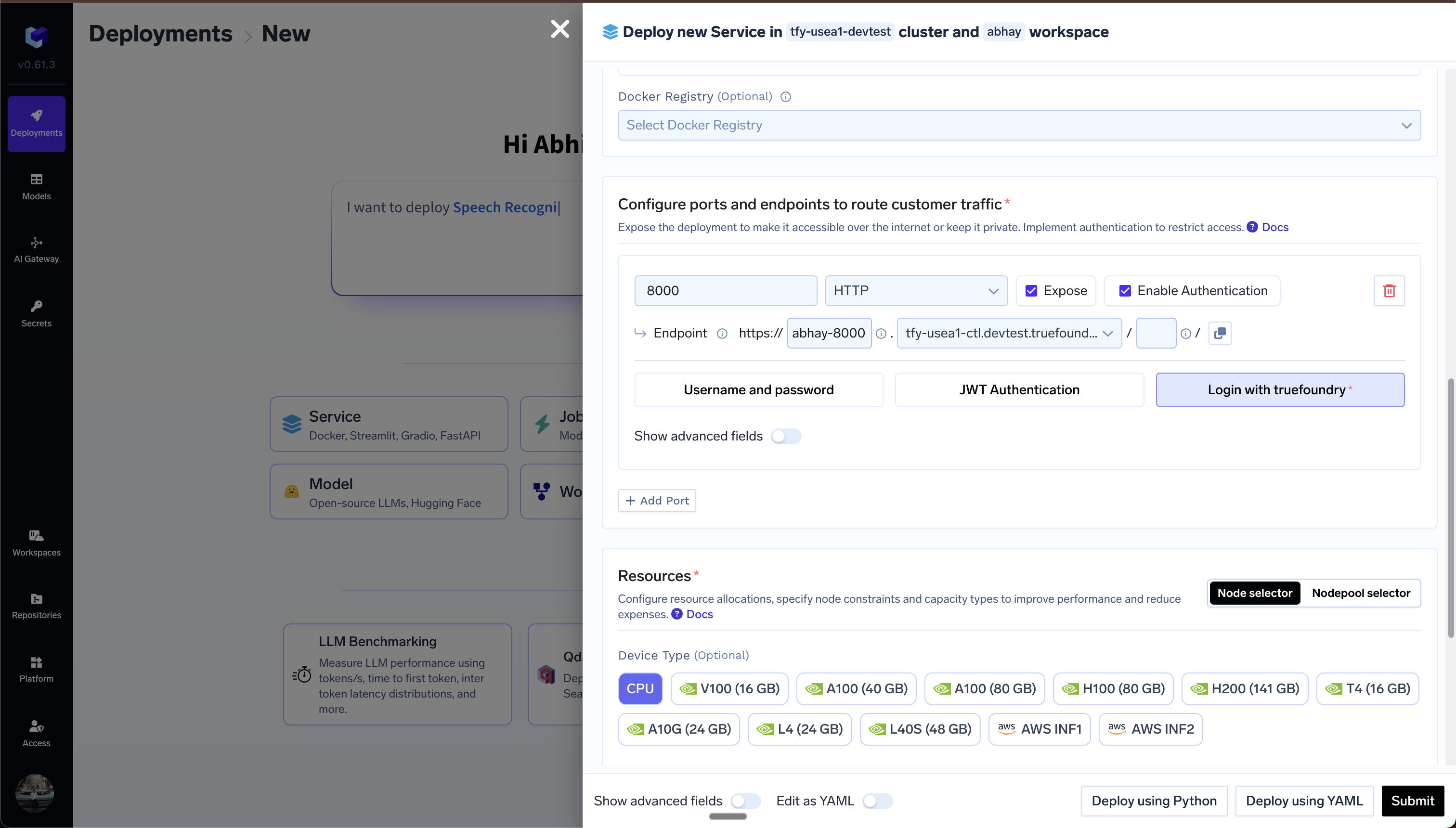
Login With Truefoundry