What is Pangea?
Pangea is a comprehensive security platform that provides API-based security services designed to protect modern applications and AI systems. It offers a unified suite of security tools that can be easily integrated into your applications.Key Features of Pangea
- AI Content Security and Guardrails: Pangea provides real-time content moderation, prompt injection detection, and toxicity analysis to protect your LLM deployments from malicious inputs and ensure safe, compliant outputs.
- Flexible Policy Configuration: Implement customizable security policies through Pangea’s domain and recipe-based configuration system with granular rules for content filtering, access controls, and behavior monitoring.
- Enterprise-Grade Security Platform: Pangea delivers a comprehensive suite of API-based security services including vault management, audit logging, redaction, and IP intelligence with seamless integration capabilities.
Adding Pangea Integration
To add Pangea to your TrueFoundry setup, follow these steps: Fill in the Guardrails Group Form- Name: Enter a name for your guardrails group.
- Collaborators: Add collaborators who will have access to this group.
- Pangea Config:
- Name: Enter a name for the Pangea configuration.
- Domain: Domain of the cloud provider and region where your Pangea project is configured. Example: if endpoint is
https://<service_name>.aws.us-west-2.pangea.cloud/v1/text/guard, the input should be:aws.us-west-2.pangea.cloud - Recipe: (Optional) Recipe key of a configuration of data types and settings defined in the Pangea User Console. It specifies the rules that are to be applied to the text, such as defang malicious URLs.
- Overrides: (Optional) Enable this option to apply custom overrides for the Pangea account configuration.
- Guard Type: Select the type of guard you want to apply from the dropdown menu.
- Pangea Authentication Data:
- API Key: The API key for Pangea authentication.
This key is required to authenticate requests to Pangea services. You can obtain it from the Pangea Console by navigating to your project dashboard and selecting “Tokens” or “API Keys” section. Ensure you keep this key secure, as it grants access to your Pangea security services.
- API Key: The API key for Pangea authentication.
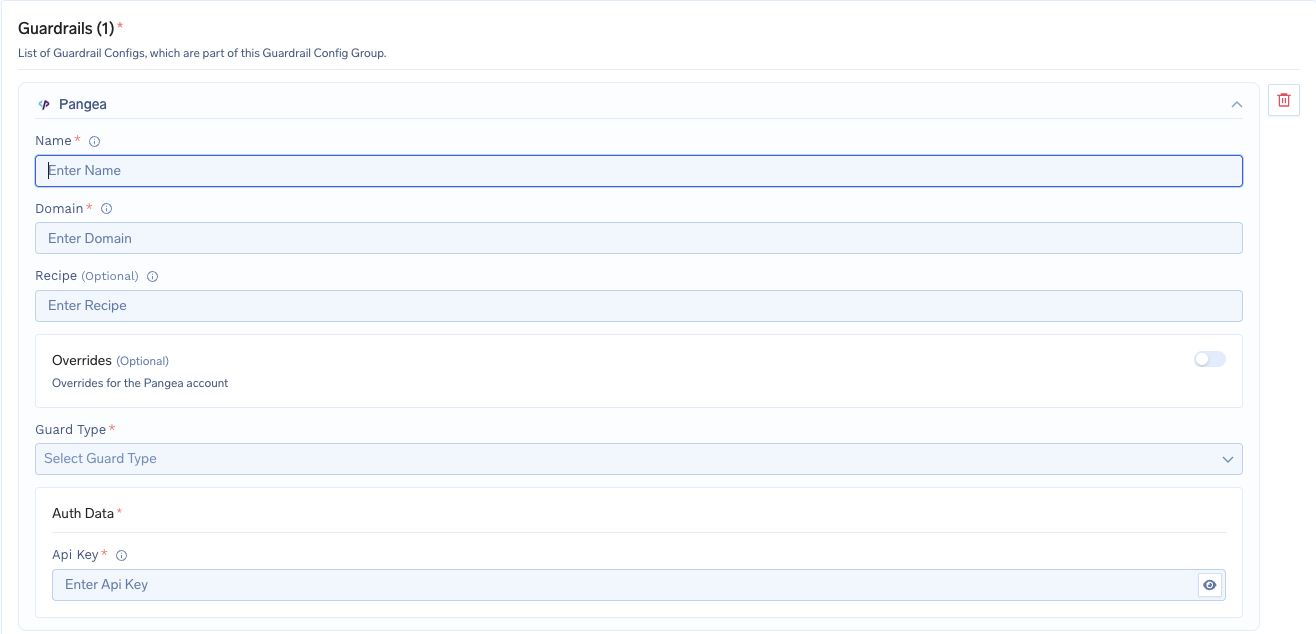
Fill in the Pangea Form
Response Structure
The Pangea API returns a response with the following structure:Example Response: Prompt Injection Detected
Example Response: Prompt Injection Detected
This is an example response from Pangea, where a prompt injection is detected. This will be blocked and a 400 error will be returned.
Example Response: Content Allowed
Example Response: Content Allowed
This is an example response from Pangea, where the content passes all security checks and is allowed.
Validation Logic
TrueFoundry uses the Pangea response to determine content safety and compliance:- If
data.blockedistrue, the request will be blocked and a 400 error is returned. - If
data.blockedisfalse, the request will be allowed to proceed.