Truefoundry gateway allows you to configure access control to models for developers, or teams or applications. This can be configured at the provider account level on our UI.
There are two permission levels when granting access to provider accounts:
- Provider Account Manager
- Can modify provider account settings
- Can add or remove models
- Can manage access permissions for others
- Provider Account User
- Can use all models within the provider account
- Cannot change provider account settings
- Cannot modify access permissions
When you assign these permissions to teams or individual users, everyone in that team (or the specific user) will receive the corresponding level of access.
Access the Models using Truefoundry API Keys
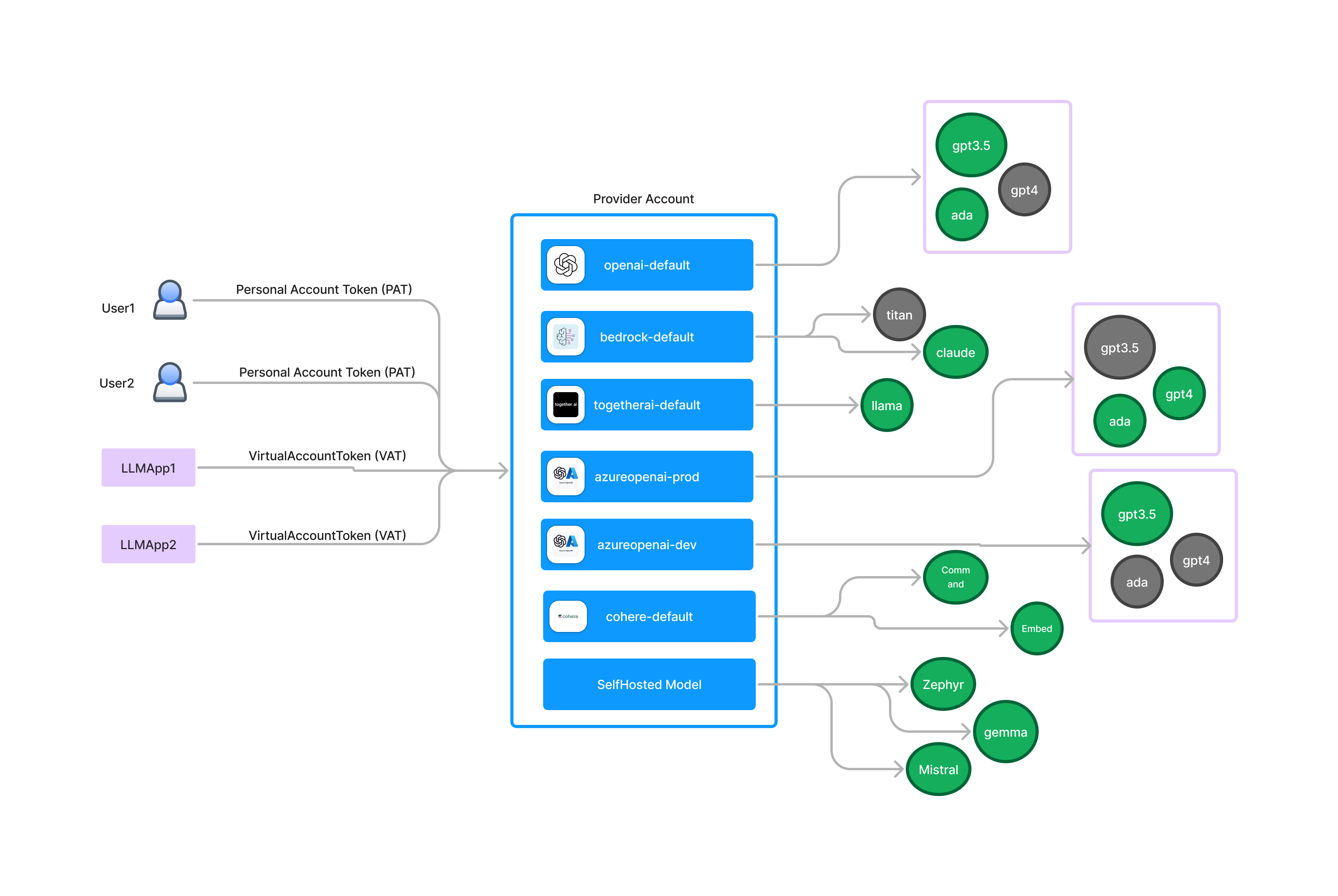 To access the models added to the Truefoundry gateway, you don’t need the keys of the original provider account like OpenAI key, or Gemini keys. Instead, you can access them by providing Truefoundry generated keys as follows:
To access the models added to the Truefoundry gateway, you don’t need the keys of the original provider account like OpenAI key, or Gemini keys. Instead, you can access them by providing Truefoundry generated keys as follows:
from openai import OpenAI
client = OpenAI(
api_key="<Enter Your Truefoundry API Key here>",
base_url="https://<truefoundry-gateway-url>/api/llm/api/inference/openai"
)
stream = client.chat.completions.create(
messages=[
{"role": "system", "content": "You are an AI bot."},
{"role": "user", "content": "Enter your prompt here"},
],
model="tfy-ai-bedrock/us-anthropic-claude-sonnet-4-20250514-v1-0",
stream=true,
extra_headers={
"X-TFY-LOGGING-CONFIG": '{"enabled": true}'
}
)
for chunk in stream:
if (
chunk.choices
and len(chunk.choices) > 0
and chunk.choices[0].delta.content is not None
):
print(chunk.choices[0].delta.content, end="")
- Personal Access Tokens (PATs): A PAT is tied to a user and has access to everything that a user has access to. This is good to be used by individual developers for testing and helps us keep track of the usage per developer.
 To read more on Personal Access Tokens, please refer to the Personal Access Tokens documentation.
To read more on Personal Access Tokens, please refer to the Personal Access Tokens documentation.
- Virtual Access Tokens (VATs): Virtual accounts are not tied to a user - instead they are virtual and we can define the entities to which this virtual account has access. We can then generate a key for this virtual account and use it in our application. This also helps us keep track of the usage per application.
Virtual accounts are a good choice to be used in applications. We don’t want to use PATs for application since its tied to a user and if the user leaves the company, the PAT will be invalid.
Its recommended to create separate virtual accounts for different applications or services.Virtual accounts can only be created and revoked by an admin in the platform.

