- Control cost per developer/team/application: Its really easy to blow up cost in LLMs because of a bug in the code somewhere or an agent stuck in an infinite loop. Hence, a good safety measure is to limit the cost per developer so that we don’t incur such costly mistakes.
- Ratelimit self-hosted LLMs: Often times, companies deploy models on their own GPUs (on-prem or cloud). However, we do want to burst to the cloud per-token API calls in case there is a sudden surge in traffic and there are not enough GPUs left to serve the requests on-prem. In this case, to avoid overwhelming the on-prem GPU, its good to setup a rate limit on the on-prem LLM.
- Ratelimit your customers based on their tier: Many products have different tiers of customers, each with a different limit on LLM usage. This can be directly modeled using a rate-limit configuration where in they can set a limit per customer.
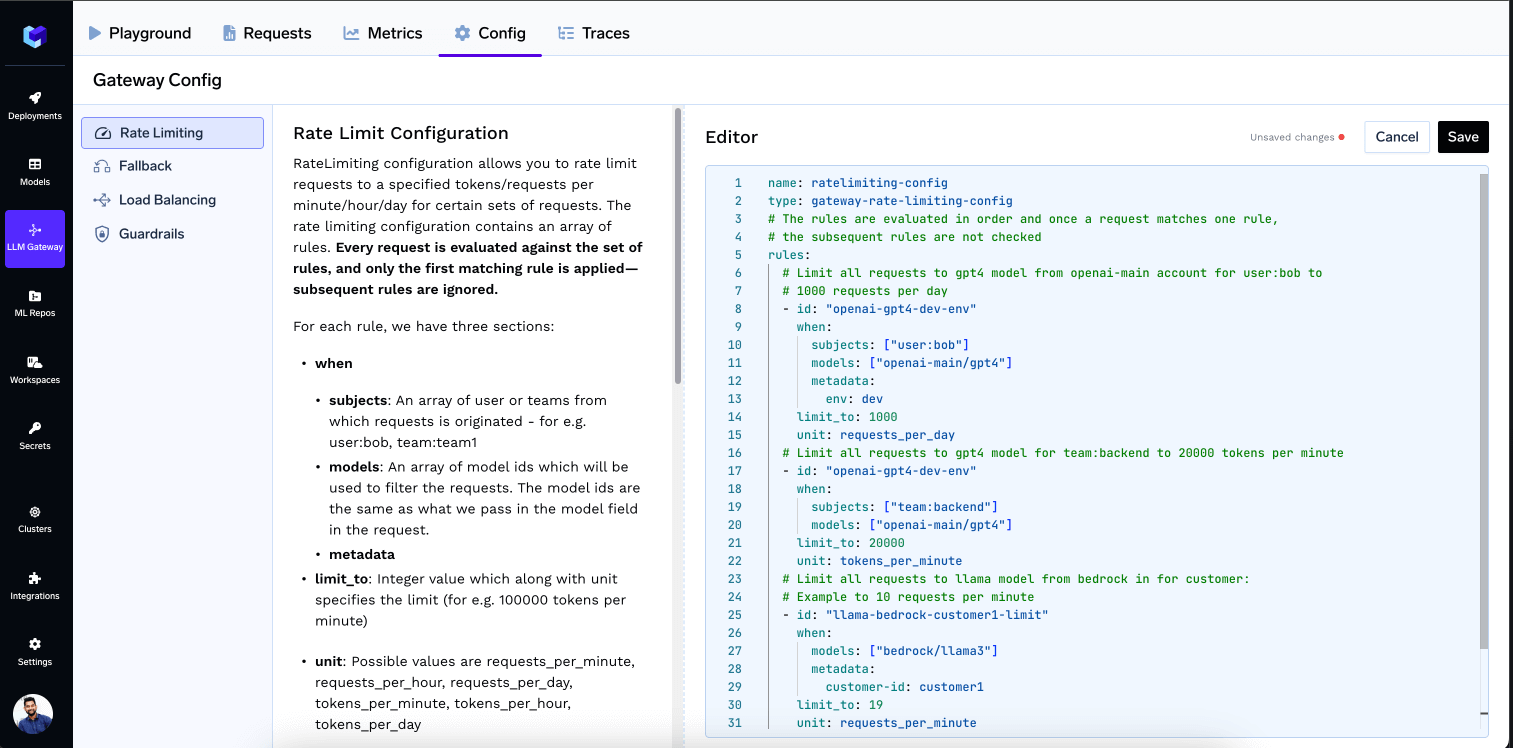
Configure RateLimiting in TrueFoundry AI Gateway
Using the ratelimiting feature, you can rate limit requests to a specified tokens/requests per minute/hour/day for certain sets of requests. The rate limiting configuration is defined as a YAML file which has the following fields:- name: The name of the rate limiting configuration - it can be anything and is only used for reference in logs.
- type: This should be
gateway-rate-limiting-config. It helps TrueFoundry identify that this is a rate limiting configuration file. - rules: An array of rules.
- id: A unique identifier for the rule. Only used for reference in logs and metrics.
- You can use dynamic placeholders that will be replaced by actual values from the request:
{user}- Replaced by the actual user making the request (e.g.,user:[email protected]){model}- Replaced by the model name being requested (e.g.,openai-main/gpt-4){metadata.key_name}- Replaced by the value of a custom metadata field sent in theX-TFY-METADATArequest header
- How placeholders work:
- If you set the ID as
{user}-daily-limit, the system will create a separate rule for each user (for example,{user:[email protected]}-daily-limit,{user:[email protected]}-daily-limit) and apply the limit individually to each one. - If you set the ID as
{metadata.project_id}-limit, and your request includesX-TFY-METADATA: {"project_id": "proj-123"}, the system will create a rule{proj-123}-limitfor that specific project. - If you set the ID as just
daily-limit(without placeholders), the rule will apply collectively to the total number of requests from all users included in the when block.
- If you set the ID as
- You can use dynamic placeholders that will be replaced by actual values from the request:
- when (Define the subset of requests on which the rule applies): TrueFoundry AI gateway provides a very flexible configuration to define the exact subset of requests on which the rule applies. We can define based on the user calling the model, or the model name or any of the custom metadata key present in the request header
X-TFY-METADATA. The subjects, models and metadata fields are conditioned in an AND fashion - meaning that the rule will only match if all the conditions are met. If an incoming request doesn’t match the when block in one rule, the next rule will be evaluated.subjects: Filter based on the list of users / teams / virtual accounts calling the model. User can be specified usinguser:john-doeorteam:engineering-teamorvirtualaccount:acct_1234567890.models: Rule matches if the model name in the request matches any of the models in the list.metadata: Rule matches if the metadata in the request matches the metadata in the rule. For e.g. if we specifymetadata: {environment: "production"}, the rule will only match if the request has the metadata keyenvironmentwith valueproductionin the request headerX-TFY-METADATA.
- limit_to: Integer value which along with unit specifies the limit (for e.g. 100000 tokens per minute)
- unit: Possible values are requests_per_minute, requests_per_hour, requests_per_day, tokens_per_minute, tokens_per_hour, tokens_per_day
- Limit all requests to gpt4 model from openai-main account for user:[email protected] to 1000 requests per day
- Limit all requests to gpt4 model for team:backend to 20000 tokens per minute
- Limit all requests to gpt4 model for virtualaccount:virtualaccount1 to 20000 tokens per minute
- Limit all models to have a limit of 1000000 tokens per day
- Limit all users to have a limit of 1000000 tokens per day
- Limit all users to have a limit of 1000000 tokens per day for each model
- Limit each project (identified by custom metadata) to 50000 tokens per hour
Configure Ratelimit on Gateway
It’s straightforward—simply go to the Config tab in the Gateway, add your configuration, and save.