Connect your Secret Store
To connect a new secret store, one needs to follow the following steps:- Navigate to the
Integrationssection of your truefoundry dashboard, and go to theSecret Storesection. - Click on the
Connect Secret Storebutton at the top right corner. - Now add the name of the secret store you want to connect. Select the Integration Provider.
- Fill in the credentials according to the selected integration provider and Submit.
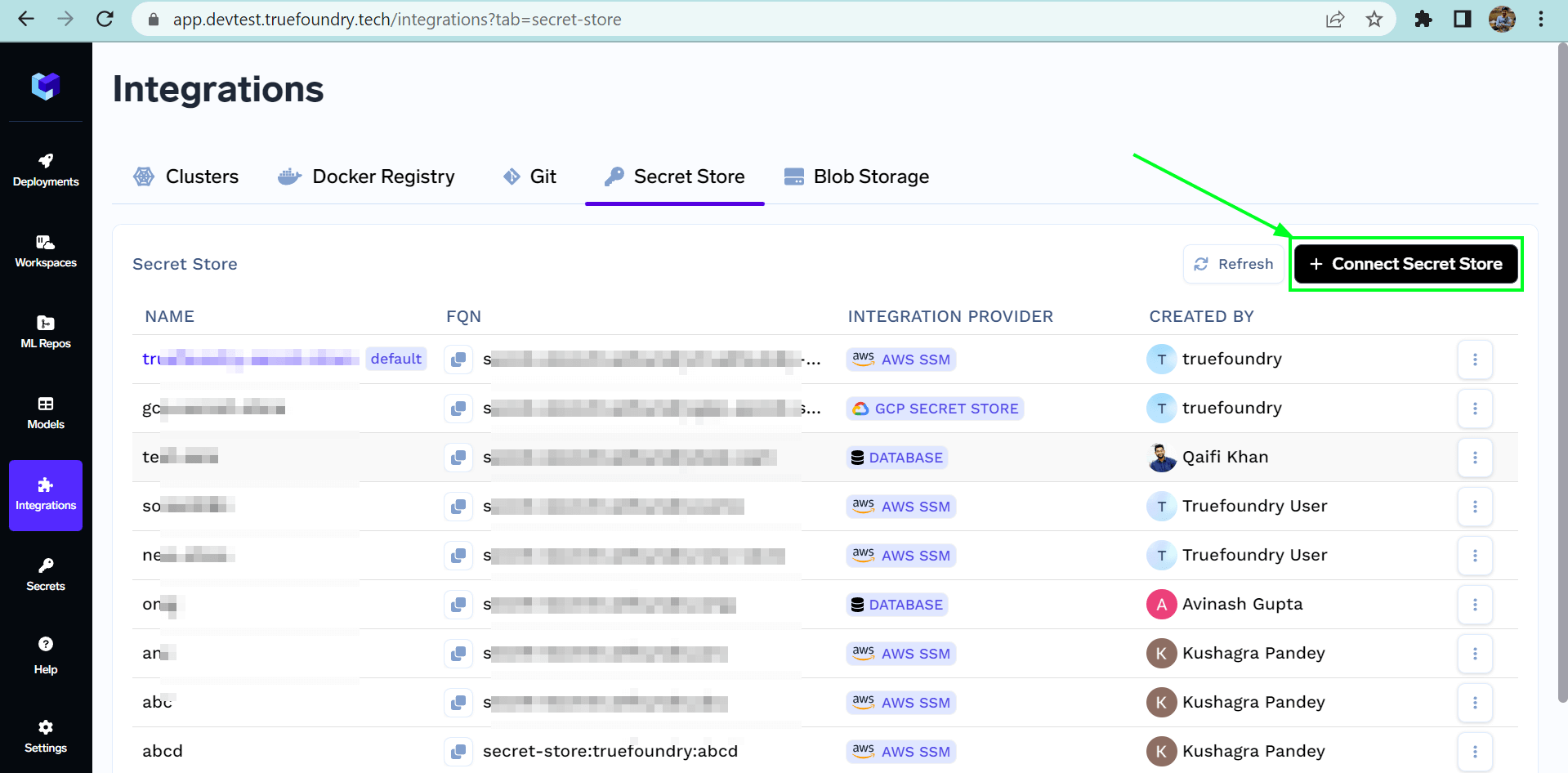
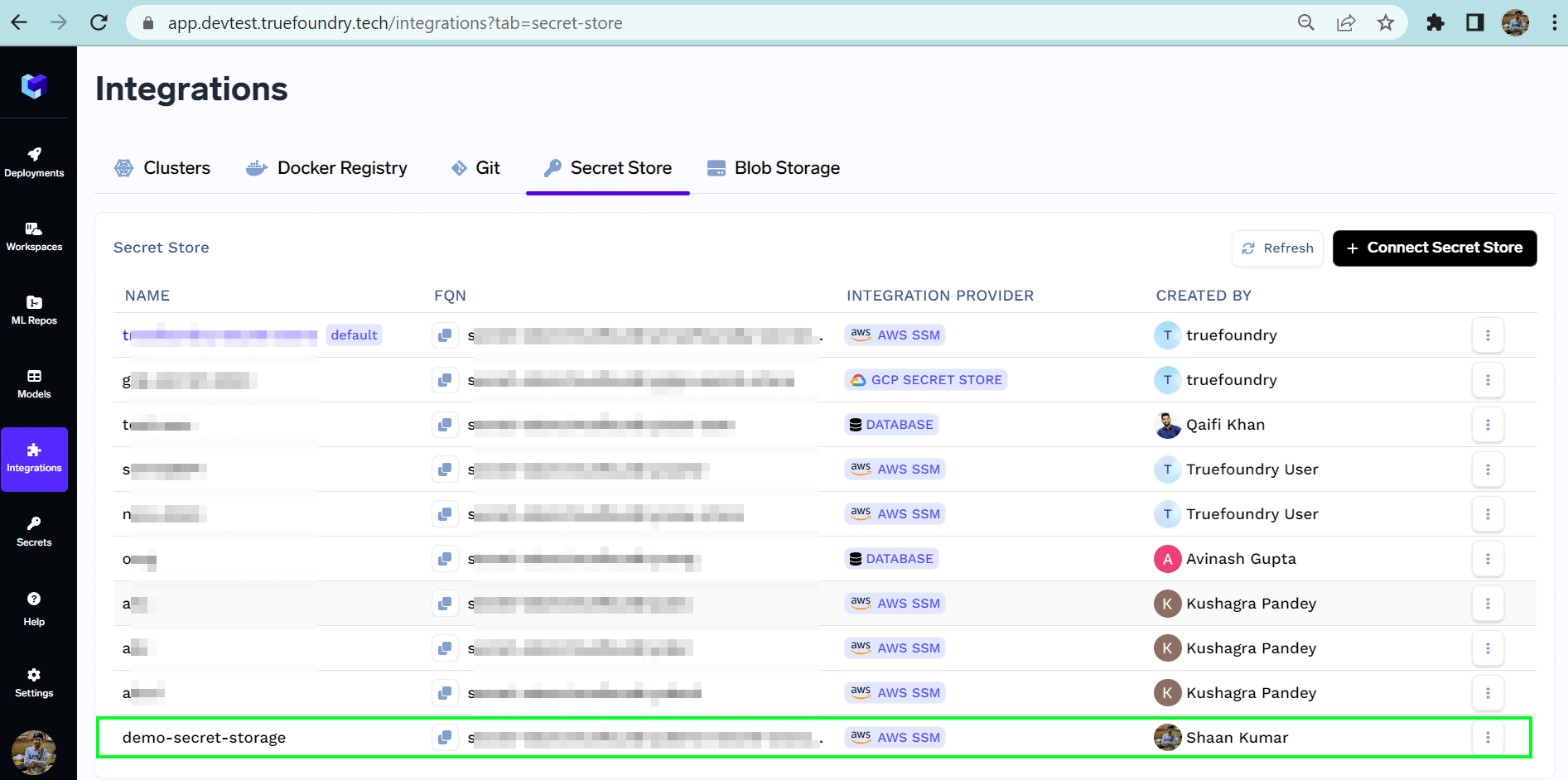
List of all secret stores
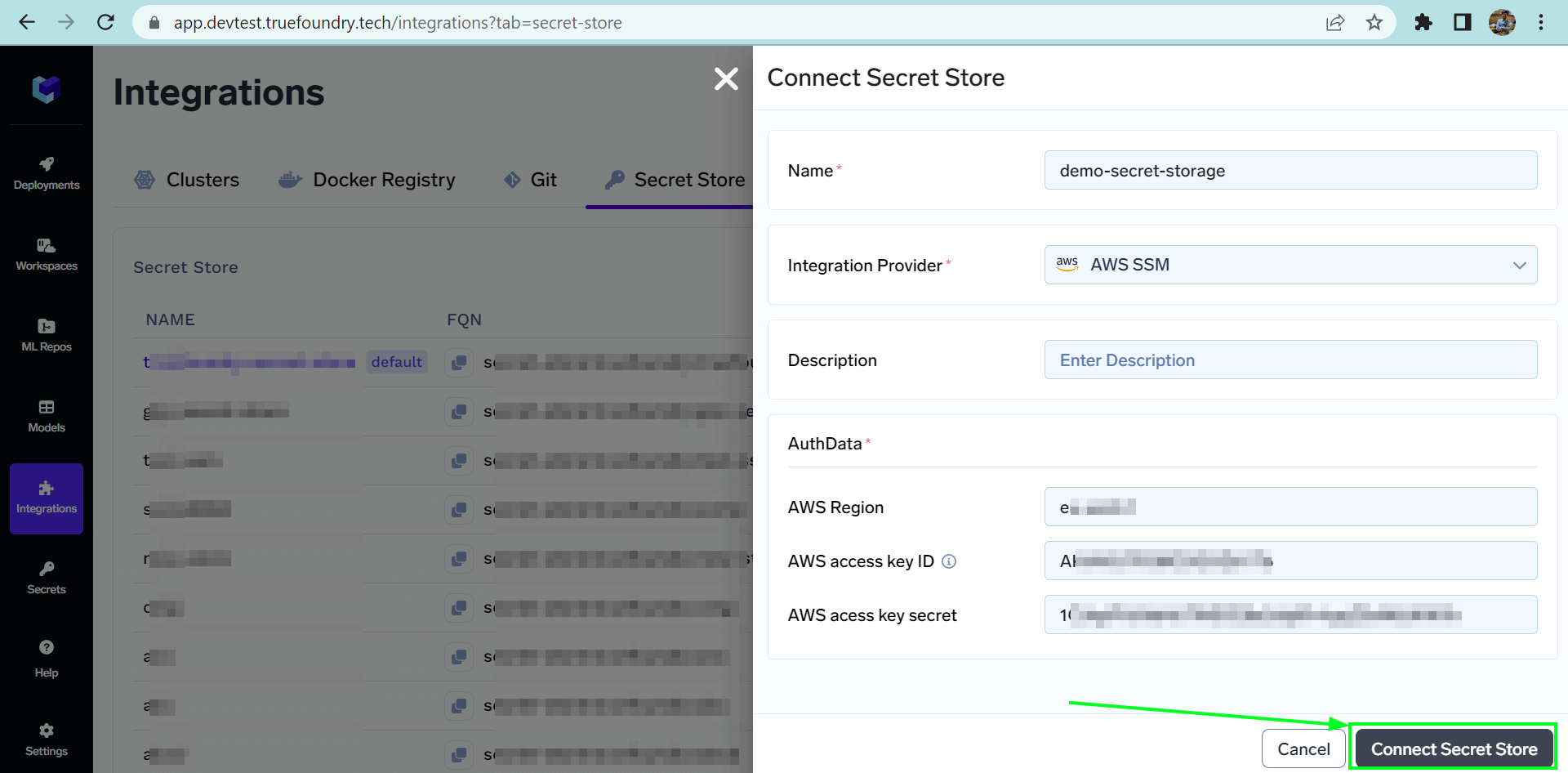
Connect AWS SSM as a secret store
Follow the steps below to connect the secrets manager to TrueFoundry:- You might have the IAM role for truefoundry already created with the name -
tfy-<short-region-name>-<name>-platform-role-<xxxyyyzzz>, if not create a new one. You can add the following permission to that role. You can also create a user with the permissions below, generate an access key and secret key and integrate the secret store via the access and secret keys.
- Navigate to Integrations > Secret Store tab and click on Connect Secret Store
- Fill in the IAM role with the correct AWS region in the form and Submit.
Connect Google Secret Manager
Follow the steps below to connect your Google Secrets Manager to TrueFoundry:-
Create an IAM serviceaccount named
tfy-<short-region-name>-<name>-platform-role, if not created before.-
Create a custom IAM role with the following permissions:
- Navigate to IAM & Admin -> Roles.
- Click + CREATE ROLE.
- Enter the name a description.
- Click ADD PERMISSIONS and add the permissions listed above
- Click CREATE.
-
Attach the custom IAM role to the service account
- In the IAM section, locate the service account created ealier.
- Click the Edit icon next to the service account.
- Click ADD ROLE and select the custom role you created
- Next to the Role, click on ADD IAM CONDITION
- Type a title, under CONDITION EDITOR tab, type in this condition
resource.name.startsWith('projects/<GCP Project Number>/secrets/tfy') - Click on SAVE.
-
Create a custom IAM role with the following permissions:
- Once the IAM serviceaccount is created, make sure to create a key in JSON format.
- Navigate to Integrations > Secret Store tab and click on Connect Secret Store
-
Paste the GCP service account
keyfile.jsonand Submit.