Step 1 (A) - Pre-requisites
-
Export important variables
-
Authenticate using
gcloud -
Set your project ID
Step 1 (B) - Enabling workload identity for your cluster
Workload identity needs to be enabled for your GKE cluster so that pods can leverage this to authenticate to GCP services without credentials.-
If workload identity is not enabled for your GKE cluster, run the below command to enable it
-
The above step will enable workload identity only in the new node pool. To enable the workload identity in the existing node pool
Step 2 - Create a kubernetes workspace
-
Export the namespace and the
serviceaccount. TrueFoundry’s workspace is analogous to Kubernetes namespace. -
Go to Workspaces tab from the left panel of the portal and create the workspace with same name as of your namespace $APP_NS
- Click on
+ New Workspaceto create a new workspace. If you already have a workspace created click on the Edit section from the right side of the workspace card. - Select the cluster where you want to create the serviceaccount and enter the name of the workspace (namespace).
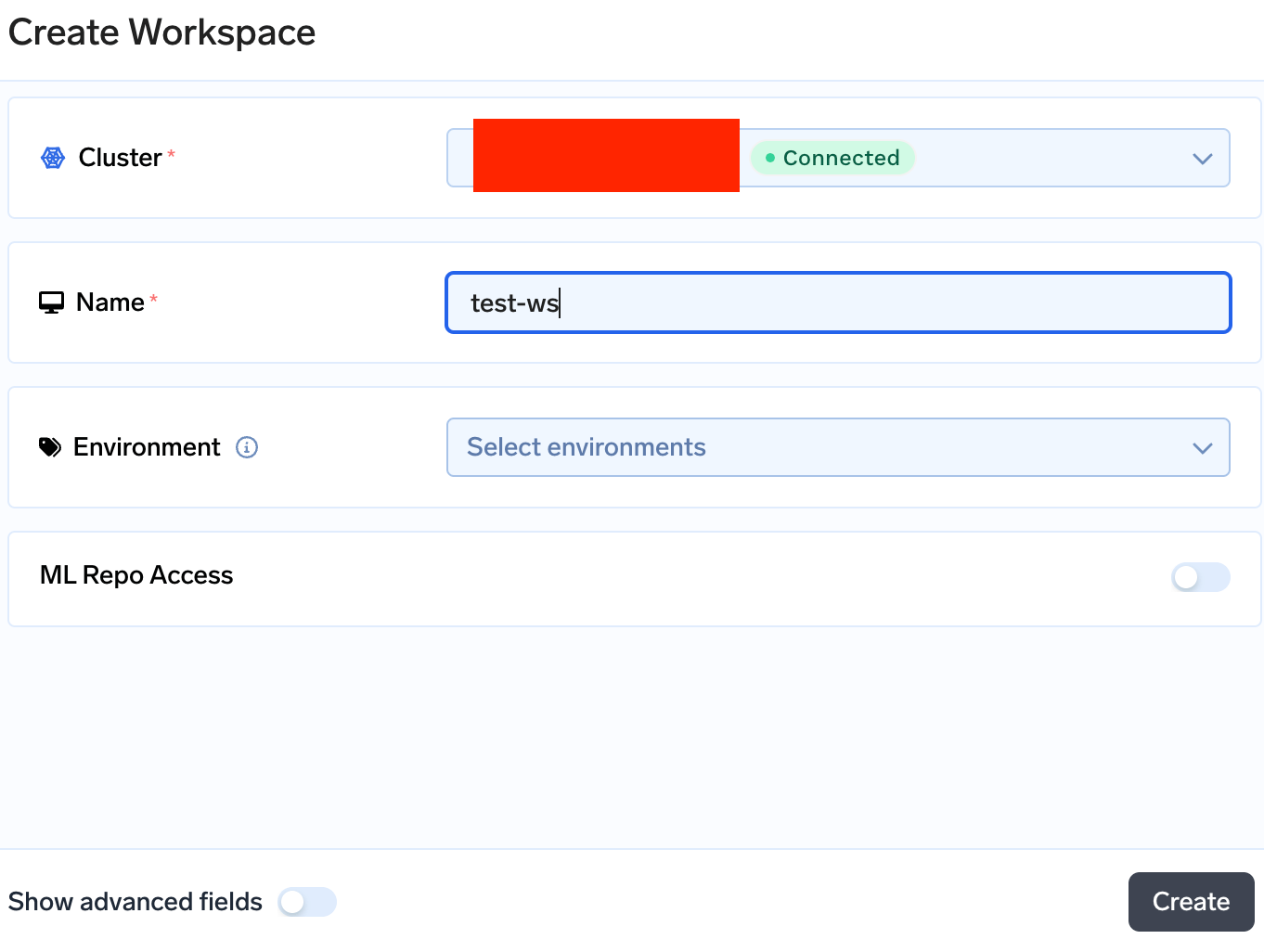
- Click on
Step 3 - Create IAM serviceaccount in GCP
In this section we will create an IAMserviceaccount which has access to buckets. We will try to use this to access the bucket files in GCP
-
Export these variables and enter the name of the google serviceaccount you want to give in the variable
GSA_NAME. We are assigning this serviceaccount Storage admin permission. You can assign the permissions that you want for accessing your GCP application. -
Create the IAM serviceaccount and assign the role using the below command. We are also assigning
roles/iam.workloadIdentityUserrole to the IAM serviceaccount on itself so that it can be accessed from inside GKE.
Step 4 - Create Kubernetes Serviceaccount in your workspace
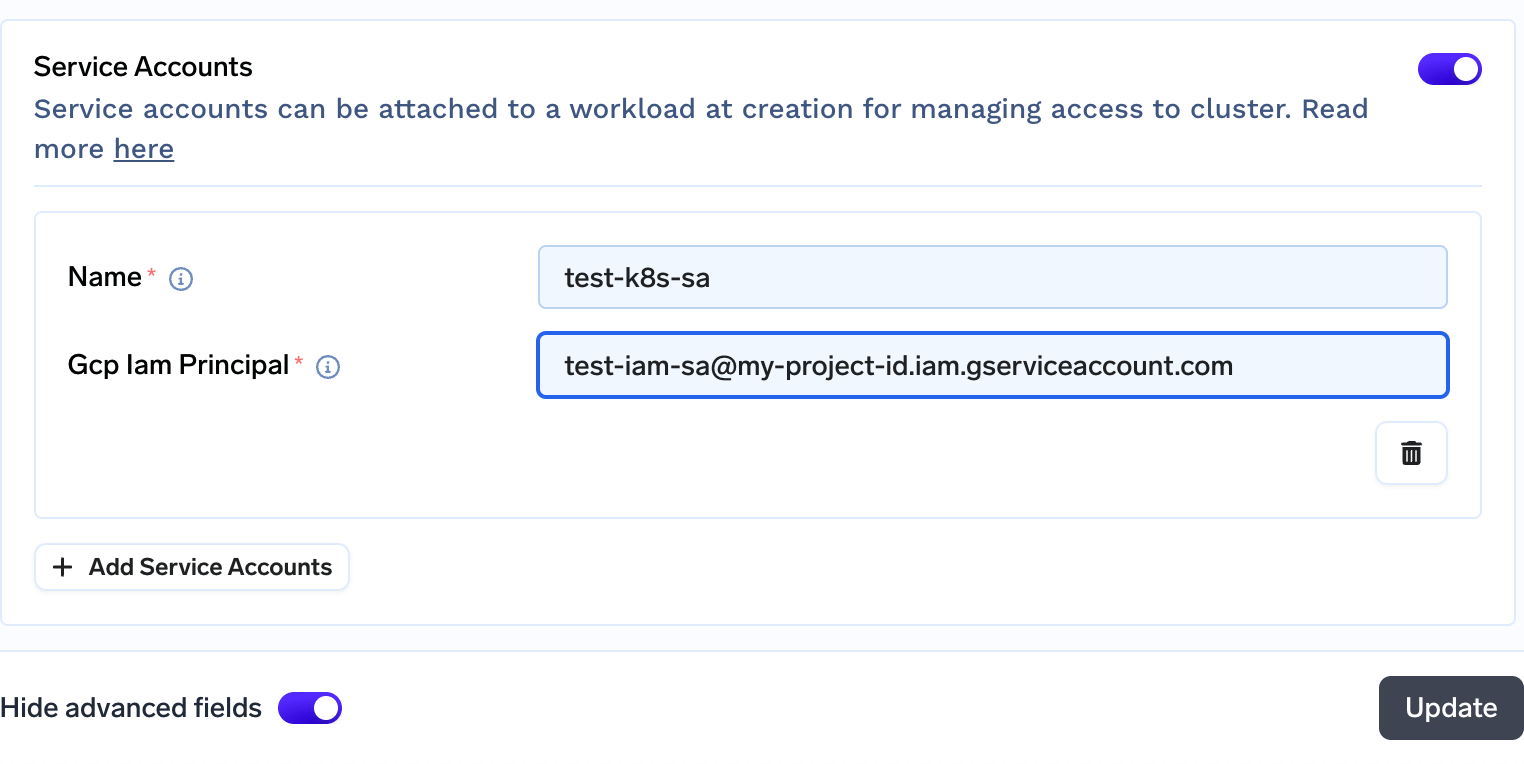
- Go to Workspaces tab from the left panel of the portal and click on the pencil icon to edit your workspace.
-
Click on
Show Advanced fieldson bottom of the screen and enableService accountsfield. -
Click on
+ Add Service Accountsto add a Serviceaccount- Enter the name of your Kubernetes Serviceaccount which is in the variable $APP_SA
-
Enter the IAM Serviceaccount name which will be
$GSA_NAME@$PROJECT_ID.iam.gserviceaccount.com
-
Click on update to continue\
Test the serviceaccount
-
Create the below pod
-
Check if you are able to list buckets without passing creds