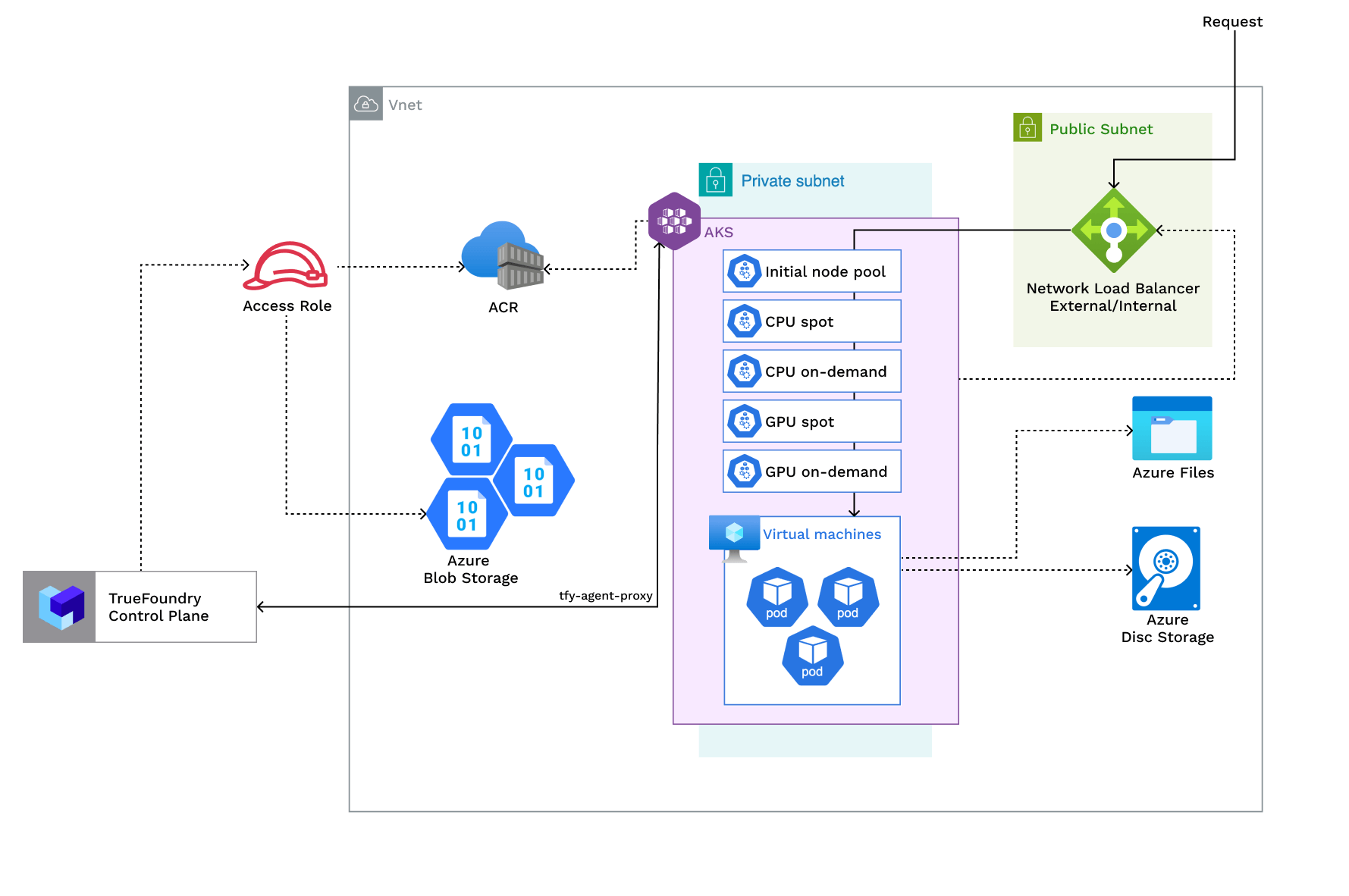
Access Policies Overview
Access Policies Overview
| Policy | Description |
|---|---|
| Access required for Azure container registry, storage account | An azure container registry is used to store the docker images for the platform. A storage account is used to store the model artifacts. |
Azure AD application with Reader and Monitoring Reader on AKS | Reader and monitoring reader permission on AKS is used to access the cluster autoscaler logs in Log Analytics and read azure node pools. User should have access to create Azure AD application. |
Requirements:
The common requirements to setup compute plane in each of the scenarios is as follows:- Billing must be enabled for the Azure subscription.
- Ensure that Microsoft.Storage resource provider is registered. Check this link for more details.
- Egress access to container registries -
public.ecr.aws,quay.io,ghcr.io,tfy.jfrog.io,docker.io/natsio,nvcr.io,registry.k8s.ioso that we can download the docker images for argocd, nats, gpu operator, argo rollouts, argo workflows, istio, keda, etc. - We need a domain to map to the service endpoints and certificate to encrypt the traffic. A wildcard domain like *.services.example.com is preferred. TrueFoundry can do path based routing like
services.example.com/tfy/*, however, many frontend applications do not support this. For certificate, check this document for more details. - Enough quotas for CPU/GPU instances must be present depending on your usecase. You can check and increase quotas at Azure compute quotas
- Ensure that host encryption is enabled.
- New network and New AKS Cluster
- Existing network and New AKS Cluster
- Existing AKS Cluster
- The new VPC subnet should have a CIDR range of /24 or larger. Secondary ranges for pods (min /20) and services (min /24) are required. Secondary range can be from a non-routable range. This is to ensure capacity for ~250 instances and 4096 pods.
- User/serviceaccount to provision the infrastructure.
Setting up compute plane
TrueFoundry compute plane infrastructure is provisioned using terraform. You can download the terraform code for your exact account by filling up your account details and downloading a script that can be executed on your local machine.1
Choose to create a new cluster or attach an existing cluster
Go to the platform section in the left panel and click on 
Clusters. You can click on Create New Cluster or Attach Existing Cluster depending on your use case. Read the requirements and if everything is satisfied, click on Continue.
2
Fill up the form to generate the terraform code
A form will be presented with the details for the new cluster to be created. Fill in with your cluster details. Click
Submit when done- Create New Cluster
- Attach Existing Cluster
The key fields to fill up here are:
Region- The region and availability zones where you want to create the cluster.Resource Group- The resource group where you want to create the cluster. Chose betweenNew Resource GrouporExisting Resource Groupdepending on your use case.Cluster Name- A name for your cluster.Cluster Versionandnode pools- The version of the cluster and the node pools to be created.Network Configuration- Choose betweenNew VnetorExisting Vnetdepending on your use case.Storage account (container) for Terraform State- Terraform state will be stored in this container. It can be a preexisting storage account or a new storage account name. The new storage account will automatically be created by our script.Platform Features- This is to decide which features like BlobStorage, ClusterIntegration using Azure AD and Container Registry will be enabled for your cluster. To read more on how these integrations are used in the platform, please refer to the platform features page.
3
Copy the curl command and execute it on your local machine
You will be presented with a 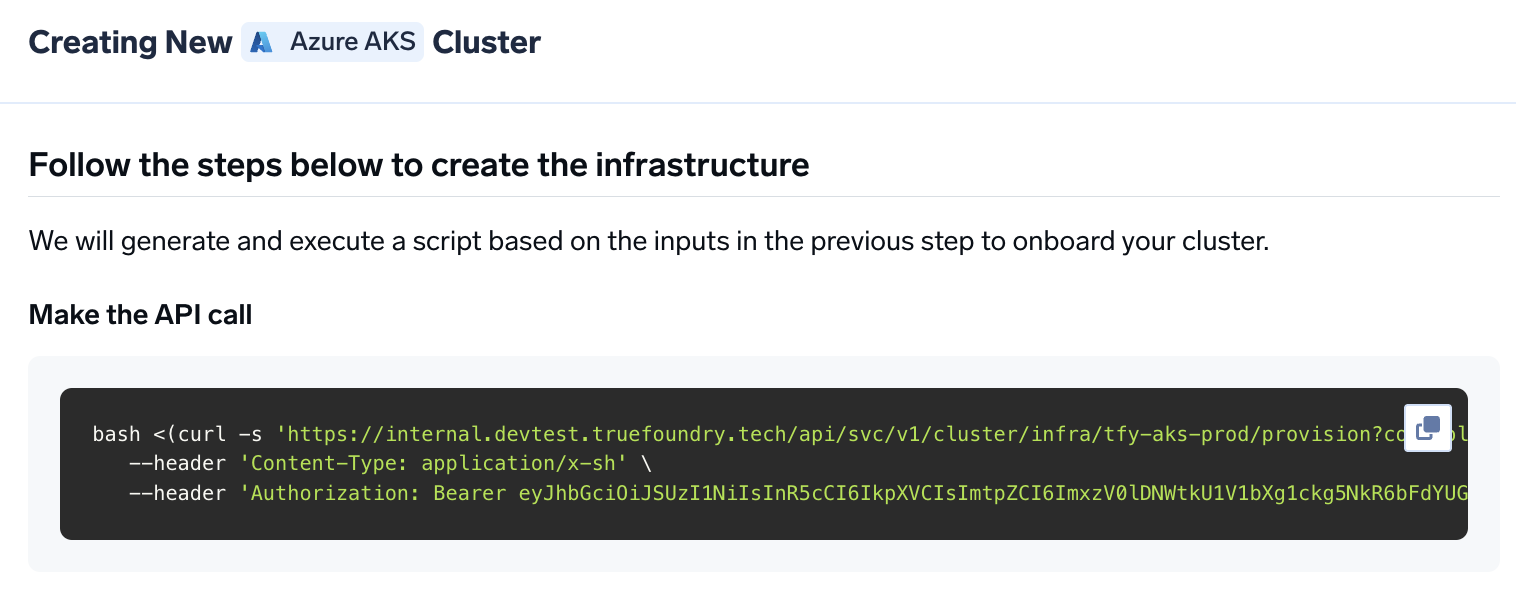
curl command to download and execute the script. The script will take care of installing the pre-requisites, downloading terraform code and running it on your local machine to create the cluster. This will take around 40-50 minutes to complete.
4
Verify the cluster is showing as connected in the platform
Once the script is executed, the cluster will be shown as connected in the platform.
5
Create DNS Record
We can get the load-balancer’s IP address by going to the platform section in the bottom left panel under the Clusters section. Under the preferred cluster, you’ll see the load balancer IP address under the 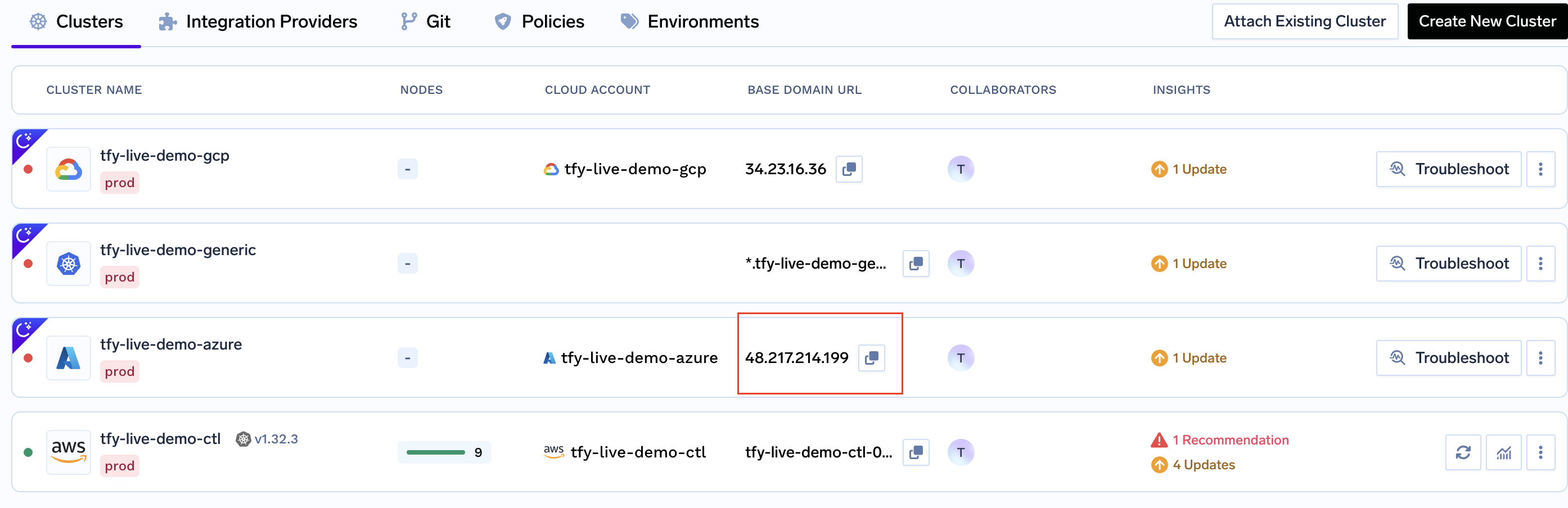
Base Domain URL section.
| Record Type | Record Name | Record value |
|---|---|---|
| CNAME | *.tfy.example.com | LOADBALANCER_IP_ADDRESS |
6
Setup routing and TLS for deploying workloads to your cluster
Follow the instructions here to setup DNS and TLS for deploying workloads to your cluster.
7
Start deploying workloads to your cluster
You can start by going here
Permissions required to create the infrastructure
The IAM user should have the following permissions -- Contributor Role to the above Subscription
- Role Based Access Administrator to the above subscription
-
Either Azure AD Administrator or Azure AD Application Developer role to:
- Create app registrations and service principals
- Assign Reader role to AD application for read-only AKS cluster access
- Assign Monitoring Reader role to applications for cluster monitoring (Ref: How to add Azure admin permission
Setting up TLS in Azure
There are two ways primarily through we can add TLS to the load balancer in Azure- Using cert-manager + Azure DNS (recommended) - Through this certs get renewed automatically
- Using Certificate and key files - Using key and certificates files