Create Guardrail Config
A guardrail configuration determines which guardrails are enforced for each request by specifying matching criteria in thewhen block. The when block allows you to target specific models, users, or request metadata, ensuring that the appropriate guardrails are applied only to relevant requests.
You can create a guardrail config by navigating to the AI Gateway -> Config Tab -> Guardrails Section -> Create/Edit Guardrail Config.
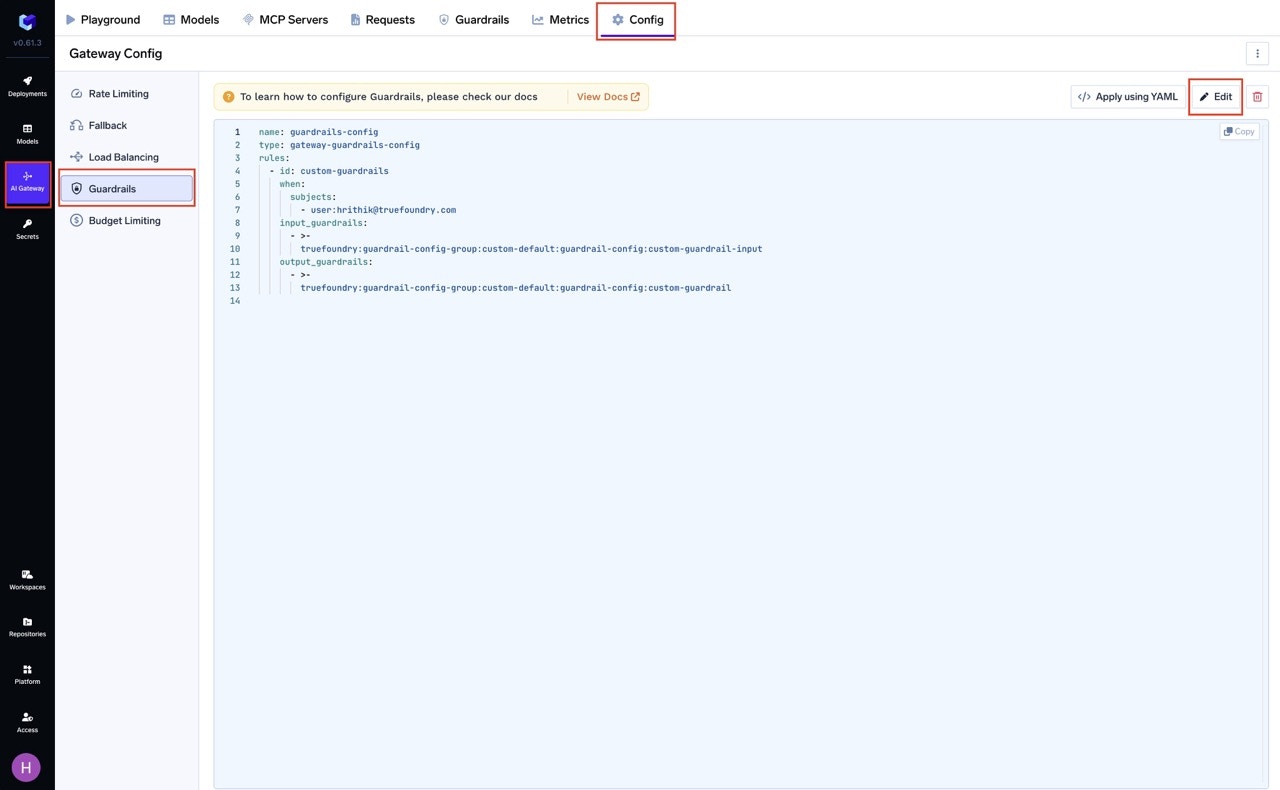
Create/Edit Guardrail Config
Config
The guardrails configuration contains an array of rules that are evaluated for each request. Only the first matching guardrail rule is applied to that request. Each rule can specify input and output guardrails that will be applied. Let’s take a look at a sample configuration first.Example Configuration
Explanation of the Example Configuration
Let’s break down the sample guardrail configuration shown above:-
name:
This is the identifier for your guardrail configuration. You can set it to any string that helps you recognize the config in logs or the UI. In the example, it’s set toguardrails-config. -
type:
This must always begateway-guardrails-config. It tells the TrueFoundry platform that this YAML file defines a guardrail configuration. -
rules:
This is a list of rule objects. Each rule determines exactly which requests it will match and what guardrails will be enforced:-
id:
A unique string to identify the rule. This helps you track which rule matched a request in logs or for future updates. -
when:
This block specifies the precise criteria a request must meet for the rule to apply. The rule will match a request if all of the following (if present) are satisfied:- subjects:
An array of user, team, or virtual account identifiers. For example,user:[email protected]matches requests made by that user.
You can also useteam:team-nameorvirtualaccount:account-nameto match requests from a specific team or virtual account. - models (optional):
An array of model names. If provided, the rule only matches requests targeting these models. - metadata (optional):
Key-value pairs to match against request metadata. For example,metadata: { environment: "production" }matches only if the request includes the headerX-TFY-METADATAwithenvironment=production. - If
whenis{}(empty), the rule matches all requests. In summary:
In the sample config, this rule will match requests made by the user[email protected]because thewhenblock specifiessubjects: [user:[email protected]]. If you addmodelsormetadatafields, the rule will only match requests that satisfy all specified conditions. If a field is omitted, it is not used for filtering.
- subjects:
-
input_guardrails:
An array of guardrail integration selectors to apply to the request input (prompt) before it is sent to the LLM. Each selector references a specific guardrail integration you have configured. -
output_guardrails:
An array of guardrail integration selectors to apply to the LLM’s response after it is received.
-
- The rules are evaluated in order. Only the first rule that matches a request is applied; subsequent rules are ignored for that request.
- Each rule can target specific users, teams, models, or metadata, and can enforce different input and output guardrails as needed.
How to get the selector of guardrail integrations
You can get the selector of guardrail integrations by navigating to the Guardrail tab on AI Gateway and clicking on the “Copy FQN” button next to the guardrail integration.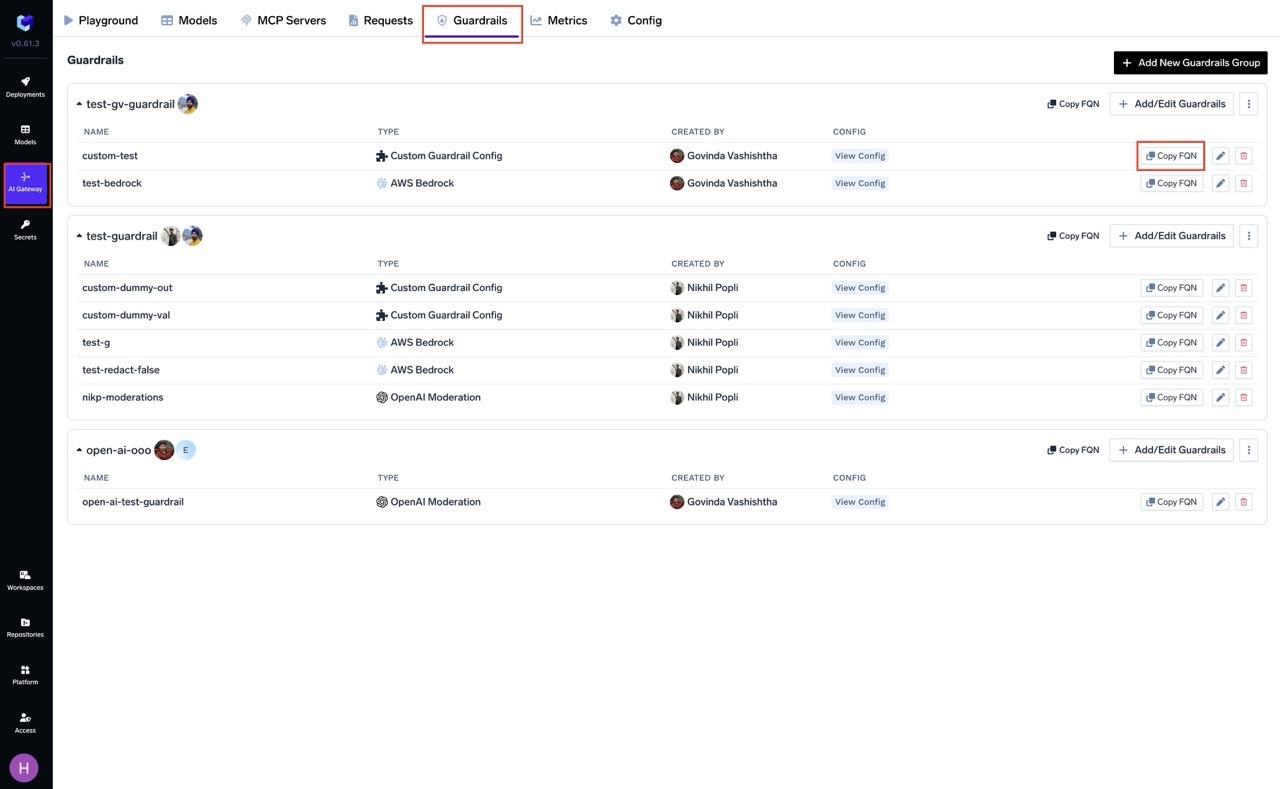
Copy Guardrail Selector